For many individuals in the tech world, gaming is the ultimate hobby.
Even if you’re playing single-player games exclusively, there’s a high likelihood that at least one of the platforms you’ve used has experienced some sort of data breach.
But what can hackers gain from gamers?
Hackers used a couple of different types of attacks against gaming companies. Some wanted to steal user accounts, while others aimed for intellectual property that they later sold on the dark web.
Overall, the number of data breaches is increasing, and the gaming industry is quite vulnerable. This article will cover what a data breach is and some of the most notable gaming data breaches in history.
What Is a Data Breach?
Data breaches are a type of cyberattack that aims to access sensitive data. However, data breaches go beyond accessing certain information. The perpetrators of this attack usually disclose this information publicly or sell it.
All industries are vulnerable to data breaches. We’ve seen corporations such as Yahoo!, Adobe, LinkedIn, and numerous other large names suffer from data breaches. At first, it’s hard to see why someone would target gaming companies rather than large corporations.
However, gaming companies and platforms harbor vast amounts of data. They range from usernames to personal and financial information.
How Data Breaches Happen
What’s common for data breaches is hackers exploiting a vulnerability to get what they want.

However, there isn’t a rule on which vulnerability that might be. For example, hackers accessed Epic Games user accounts because of an outdated website.
On the other hand, Naughty Dog, the company behind The Last of Us, suffered a data breach because of a security flaw in one of the previous versions of their game.
So, one of the first stages of a data breach is finding a vulnerability in a specific system. This can be technical, such as the two previously mentioned examples. On the other hand, some hackers look for high-level personnel whose credentials are used to get inside access to a system.
After finding the vulnerability, hackers try to make initial attacks and test their grounds. Once they get the information they want, the attack is considered successful.
What Is Targeted in Data Breaches?
Gaming platforms can have millions of users. Each user’s account can be connected to payment methods such as credit cards or electronic wallets.
Hackers can access one account to obtain their other accounts as well. Chances are that the user is using the same email and password for their email or social media accounts. This should be your reminder to go ahead and update your passwords to be strong and random.
The accounts themselves can also be quite valuable. Since even free-to-play games have microtransactions, accounts can differ in value because of the in-game cosmetics, ranking system, or other game-related measurements.
We’ve seen individuals sell Fortnite accounts worth anywhere from $1 to hundreds of dollars.
However, hackers aren’t only targeting individual accounts. While they can benefit from harming users, others attack the company directly. For example, the hacker who got their hands on The Last of Us Part 2 information leaked it online.
On the other hand, the individuals behind the attack on Capcom asked for a ransom of $11 million for their data to be returned. Capcom refused to pay the ransom, and thus, the data was leaked on the internet.
In conclusion, hackers have multiple targets when conducting a data breach. User data and sensitive information are valuables they can earn money from, but some conduct breaches without even making a profit.
Why Gamers Should Beware
Individual gamers can be targets of various cyber attacks, like companies.
An increase in the amount of money involved in microtransactions makes gamers attractive targets for hackers. The amount of data that gaming companies have is growing.
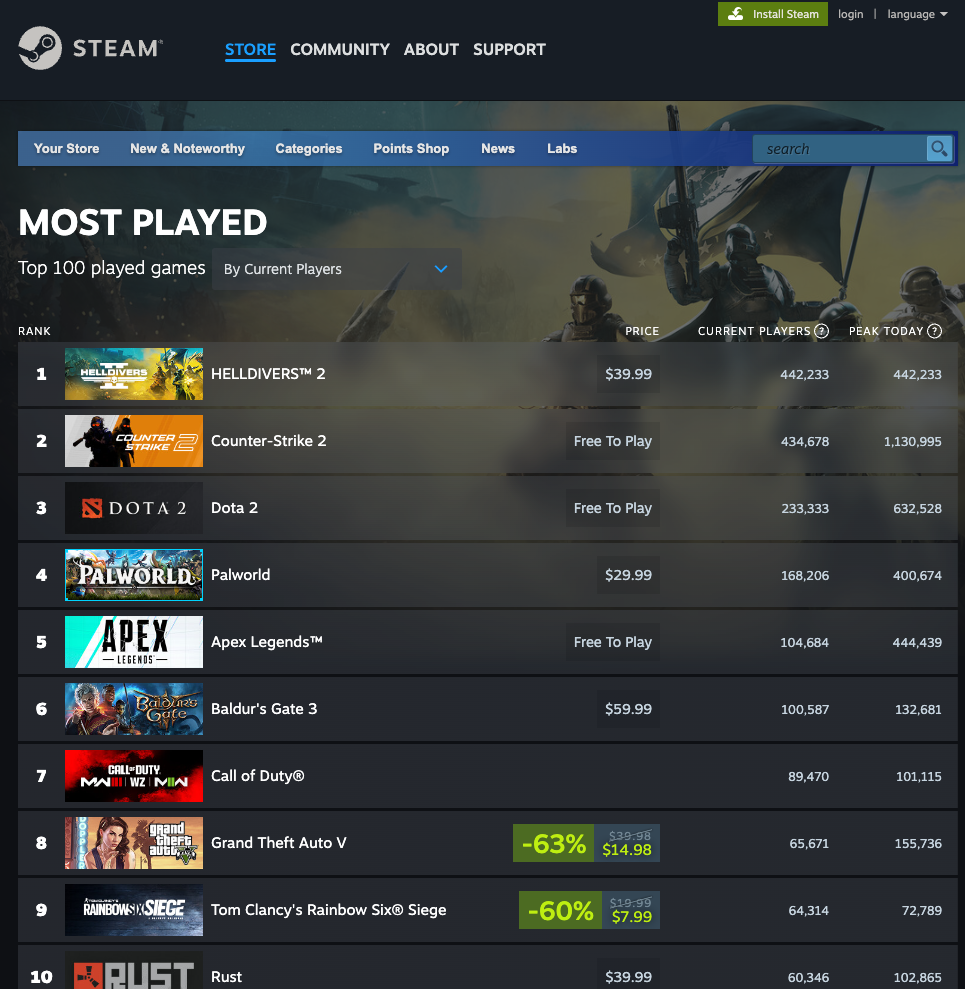
Furthermore, games often have mechanics that allow others to see individual accounts’ worth. This can sometimes lead to being extensively targeted by hackers.
Because gaming companies have shown that they can be profitable for attacks, gamers should be more careful about where they leave their information.
Limiting the amount of data that you’re sharing and avoiding platforms that are known for security leaks are easy first steps to increased security.
The cost per data breach amounts to an incredible 9.48 million dollars, which isn’t a drop in the bucket for any gaming company.
Methods of Attack Against Gamers
Gamers are often targeted through phishing attacks by malicious individuals who pose as legitimate company personnel. Other methods include targeting gamers through fake promotions or “in-game currency generators.”
To defend against this, individuals generally must have a certain degree of cybersecurity knowledge. Knowing how to spot fraudulent attempts is one of the best ways of avoiding them altogether.
Don’t worry if you aren’t a cybersecurity expert. A simple install of a VPN like Windscribe before launching your favorite game can help protect you online.
As for the attacks targeted towards companies, the methods used were mainly based on finding and exploiting vulnerabilities. It seems gaming platforms need to pay more attention to their cybersecurity.
Gaming companies also suffer from DDoS attacks. These cyber-attacks aim to overwhelm the servers and make the services unavailable to gamers and personnel.
Worst Gaming Data Breaches of All Time
There are numerous gaming data breaches that we can talk about. From indie development companies to multinational corporations, hackers will target both large and small organizations.
Why? They’re looking for low-hanging fruit.
Let’s dive into some of the most notable examples we’ve seen and what impact they’ve had on the companies and the fanbase.
Half-Life 2
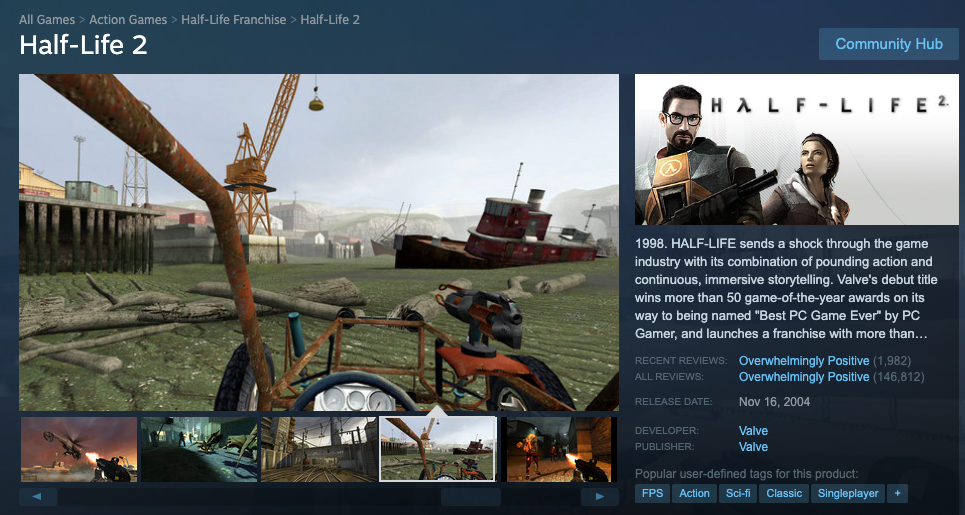
If you’re a gamer, it’s unlikely that you haven’t heard about Half-Life 2. This is one of the most recognizable franchises from the early 2000s. This franchise also gave birth to games such as Counter-Strike, Team Fortress, and Day of Defeat, which started as Half-Life 1 mods.
Because of the success of the first Half-Life game, the second instance was long-anticipated. Valve, the company behind Steam and numerous game franchises, was hacked in 2003 by a German-based hacker.
The hacker didn’t have any malicious desires behind the attack. While many people want to profit from such endeavors, the perpetrator only wants to see the game before anyone else. His love for Half-Life drove him crazy, and he got caught because he apologized in an email to Gabe Newell, the founder of Valve.
He shared this game’s source code with another person who leaked it online. This has been one of the first high-profile hackings in the gaming industry. Although this was troubling at the time, Half-Life 2 is one of the best-rated games of all time, and it’s sold 6.5 million copies.
Nintendo Gigaleak
A significant name in the gaming world, Nintendo has been around for more than a hundred years. While starting as a company that produced playing cards, nowadays, it’s popular for franchises such as Legend of Zelda, Pokemon, Super Mario, and Donkey Kong.
Furthermore, Nintendo has also developed numerous gaming consoles, such as the Game Boy, the Nintendo DS, the Wii, and Switch.
A series of data leaks started in 2018, with the “Gigaleak” referring to one of the more prominent instances that occurred in 2020. This instance has been three gigabytes in size, and while this doesn’t seem like much data, it’s quite significant.
Many of the leaked data comes from early Nintendo projects, which were smaller in size. The leaks also included projects on which Nintendo was working at the time.
The leaks started happening on an anonymous image board called 4chan, with Nintendo acknowledging them in 2022.
Multiple suspects could be behind this, and Nintendo believes that many of the leaks come from third-party companies they’ve contracted with.
Overall, Nintendo Gigaleak is considered a positive event in some communities. The code released in these leaks allowed programmers who work on video game preservation and emulators to do their work better.
However, this data leak is still a crime that’s being looked into.
Sony (2011 & 2014)
In 2011, Sony, a company behind one of the most popular consoles in the world, suffered a significant data breach. The so-called PlayStation Network outage was an attack that led to an outage that lasted 23 days and leaked more than 77 million accounts.
The losses that the company suffered were immense, being as high as $171 million. Furthermore, Sony suffered a significant blow to their reputation. Sony reacted by compensating users and changing terms and conditions, but the attack wasn’t without consequences.
While many of the data breaches occurred to steal account or video game data, the 2014 Sony security leak had much higher stakes. During this attack, a hacker group released data about numerous Sony employees and their families, copies of unreleased films, and various other information.

The hacker group demanded that a movie called “The Interview” be withdrawn. The movie was about North Korea and Kim Jong Un, and it’s speculated that North Korea was behind this cyber attack on Sony.
How to Keep Your Data Safe
There isn’t a one-size-fits-all solution to protecting yourself online. There are numerous ways in which your data can be targeted. However, it’s crucial that each of us individually do what’s in our power to defend against these threats.
This article breaks down some of the most notable gaming breaches in history, and we can see their impact on the industry. Furthermore, it’s essential to realize that gamers are the underlying victims. In other words, you need to understand the common risks of gaming online and how to defend yourself against these risks.
That’s where real-time protection in the form of an antivirus and VPN can significantly boost your security. If your account is on the list of breached credentials, you should check your accounts and switch to a password manager or manually update your compromised passwords.
You should understand what the different types of authorization are and turn on multi-factor authentication for all platforms where you can and avoid downloading games from unreputable platforms.
Are you ready to take action today to protect yourself when playing your favorite game? Download Windscribe VPN today, and you’ll be gaming blissfully in no time.




