So, you look like Leonardo DiCaprio and like to get dressed up like a pilot and fly around, maybe put on a stethoscope and perform a few routine examinations in the name of cashing a few cheques? This makes for a great plot to a Hollywood film, but not all identity theft is fun and games!

Cosplay aside, our ability to take the form of another person has never been easier, thanks to the sheer volume of personal information we leave online. Accidentally clicked a link in a phancy phishing email? Took a Facebook birthday quiz? Made the choice to be environmentally-friendly by reusing your password over and over again? All of these can help thieves and con artists to moonlight as you.
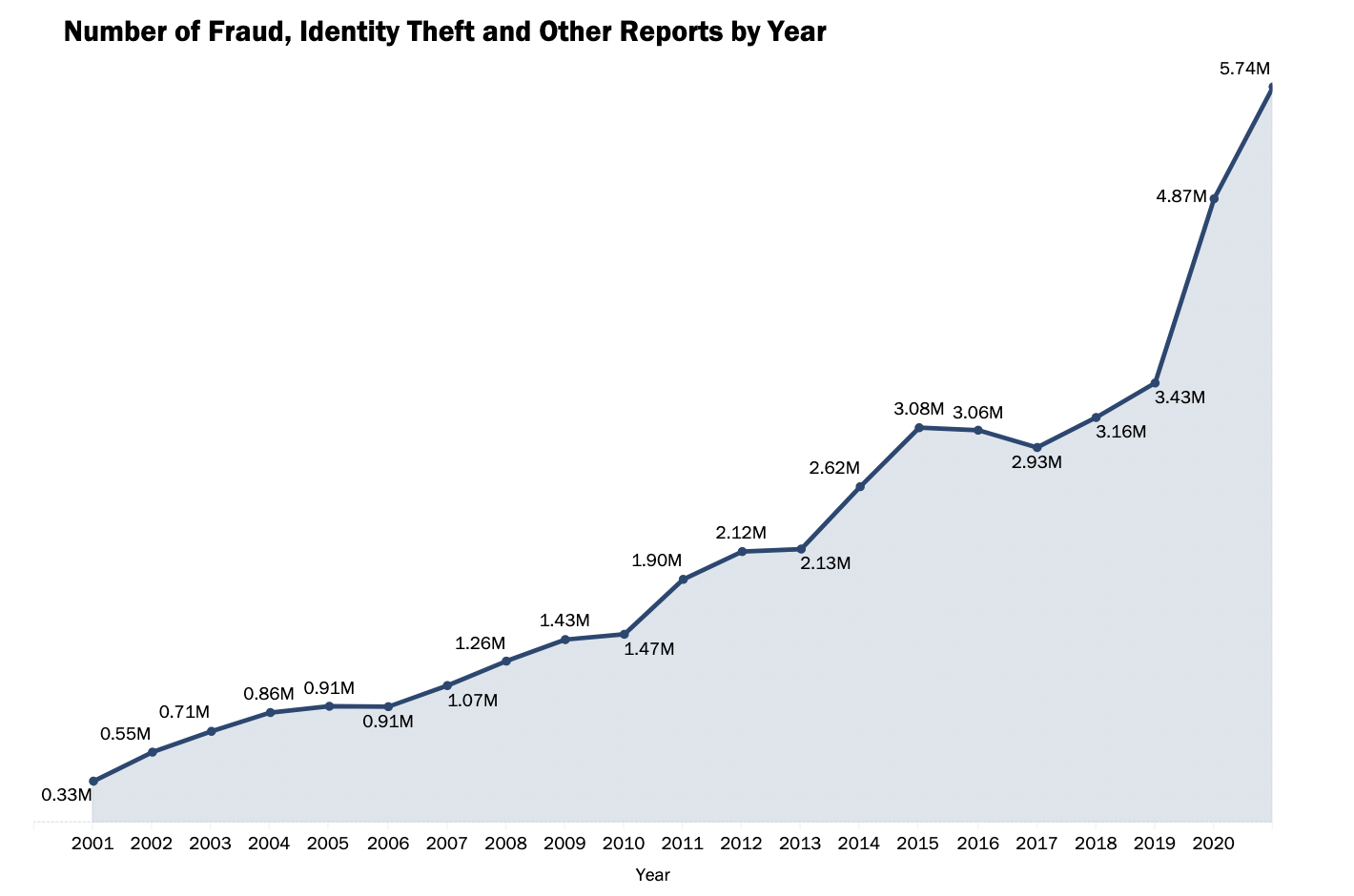
Naturally, this has caused a huge spike in the number of identity theft reports each year, with cases jumping to over 5.7 million cases in 2020 in the US alone, up from just 1 million in 2007.
While most cases of identity theft result in losses of around $500, there are some spectacularly crazy and, admittedly, exciting cases where colossal corporations, cromulent celebrities, and can-you-blame-em children have been defrauded of millions of dollars. Let’s examine the top 3 and spook each other out.
Exhibit A: Public Library Enemy #1
Back in 2001, we saw one of the first big public cases of identity theft in the digital age, perpetrated by Abraham Abdallah, a busboy who defrauded over 200 celebrities and public figures using a computer in the Brooklyn NY Public Library.

Like something out of a Hollywood blockbuster, Abdallah used an old dog-eared copy of Forbes magazine featuring the “400 Richest People in America” to target a star-studded cast that included the likes of Steven Spielberg, Oprah Winfrey, Warren Buffet, Michael Bloomberg, and even celebrated Ewok patriarch, George Lucas.
Abdallah’s hi-tech scam began with a basic series of credit report requests from ‘trusted’ providers Equifax, TWR, and Experian. After duping those companies, he had obtained social security numbers, credit card numbers and all vital financial records that would allow him to play every leading role in his own celebrity show. He assumed the identity of each of his showbiz victims using their credit cards as his own, accessing their brokerages, and opening new accounts across the world.
Abdallah tracked packages that he ordered in his victims' names all over the US via an intricate network of web-enabled mobile phones and virtual voicemail services, all from the safety of his library computer lab. He used couriers (and even prostitutes) across New York City to deliver the expensive and exotic fruits of his labor (surely Yubari king melons).
His scam was working so well, Abdallah decided to swing for the fences by requesting a 10 million dollar transfer from the account of one Thomas Siebel, founder of Siebel Systems (the dominant CRM provider of the 90s, acquired by Oracle for $5.7 billion, no biggie), to a newly opened Australian account. This would have worked if Siebel had actually had the money. Merril Lynch called Siebel’s people to make sure he wanted that much money moved, which sounded the alarm bells everywhere.
Police traced everything they could for the newly greenlit Operation CEO, starting with two Yahoo! email addresses. This led to the discovery of forged documents, voice mail recordings, and the PO boxes that they would eventually stake out. They intercepted and commandeered a shipment of credit card duplication machinery destined for Abdallah, then posed as couriers to arrange a delivery. He was cornered and arrested in his SUV in a suitably Hollywood style , with the arresting officer jumping on top of Abdallah’s moving vehicle and dangling from his sunroof.
The dog-eared copy of Forbes was found on the scene. Beneath their Hollywood photos, scrawled in pen, were social security numbers, credit card info, bank balances, and in some cases, even their mother’s maiden names. Some $22 million dollars was in play when he was finally caught.

If there is anything to learn from this, it is that identity theft doesn’t discriminate: it affects us all. CNN reported that there was a new victim of identity theft in the U.S. every two seconds in 2016, a number that has multiplied each year since as we move further into the digital age. Even Microsoft co-founder, Paul Allen, whose own name was on the PO boxes receiving the deliveries, had no clue they had been scammed until they were told by police.
The way Abdallah was able to succeed was through his interception of private information. In 2001, much of that information was moving physically, via fax and telephone. In 2023, almost all of our information is online - whether we like it or not - making it even easier to intercept with the right tools.
You should always be careful where you are sending your information; encrypting that information with a VPN will help take the guesswork out, leaving you far less susceptible to the more common digital versions of attacks like Abdallah’s.
Exhibit B: Synthetic Identities
Our next case follows the trail of Cory Cato, a 41-year old Georgia native who was busted in 2022 for creating “synthetic identities”. Cato and his gaggle of gangsters gathered the personal information of real people – social security numbers of children, mostly - that were then forged into some cyberpunk-esque fake people, with made up birthdays and names, and some very real incoming money problems. These newly minted identities were then used to open credit cards, bank accounts, and more. Imagine your first week as a person, and you’re already in debt!? At least let people enjoy their bad decisions, like I did in college!

Much like his predecessor, Abraham Abdallah, the key to Cato’s nationwide fraud ring was a commercial mail receiving agency called Pak Mail, which he maintained in the heart of the Peach tree state. It was there where he and his co-conspirators collected all of the actual paperwork and statements for these manufactured individuals and, of course, spent the funds from their ill-gotten gains.
While there isn’t much information on how Cato got caught, we do know that one of his 11 co-conspirators, Turhan Armstrong, drew the attention of US homeland security after failing to report any income for multiple years during the scam. Pay your taxes, people! Turhan himself racked up a bill of over 3 million dollars, while Cato’s total ended up around 2 million, defrauded from various banks & lenders. Every penny stolen was ordered to be paid back as restitution, in addition to his 94 month sentence for conspiracy to commit financial institution fraud & aggravated identity theft.
As per the Attorney General’s office: “[Cato] and his co-conspirators built their wealth off the backs of the people whose identities they stole, many of them children,” prosecutors argued in a sentencing memorandum. “Both the effects on these victims’ credit histories and their sense of violation are impossible to quantify, but they provide further reminder of the seriousness of [Cato’s] crime and the callousness of his conduct.”
Keeping an eye on your data is huge and is maybe the most important step to keeping yourself safe or remedying identity theft. In this case, no one thought to check the credit reports of Cato’s victims, you know, because they were kids. According to a 2017 study conducted by Javelin Research, more than 1 million children had their identities stolen, and 66% of victims were under the age of 8. A study from the Center for Cyber Safety and Education revealed that 40% of children in grades 4-8 have talked to a stranger online. Even worse, 53% provided their phone number to that person! Talk to your kids about cybersecurity early and often.

Advise the youths in your household to keep their (and your) credit card information to themselves and opt out of storing it online when shopping or making (terrible) microtransaction in-game purchases on their phone. If your teen has access to their SSN/SIN, urge them never to provide that information online. Teach them about phishing, teach them about the strength of a good password, too.
This is a nice reminder for us (pretend) adults, too, as we’re certainly not immune from bad decisions. According to Aite Group’s latest research on U.S. Identity Theft, around 47 percent of Americans had suffered financial identity theft by 2020. Some are hardly even at fault, as digital criminals are making it harder to know what is real and what isn’t.
Ross J. Anderson, Professor of Security Engineering at the University of Cambridge, describes social engineering (in the context of internet security) as the “psychological manipulation of people into performing actions or divulging confidential information”. A great example of this is the use of the "forgot password" function on most websites which require login – an improperly-secured password-recovery system can be used to grant a malicious attacker full access to a user's account, while the original user will lose access to the account.
Exhibit C: Attack of the Clones
Likely the largest socially engineered attack so far was carried out by 48 year old Lithuanian Evaldas Rimasauskas, between 2013 and 2015, netting over 120 million dollars from two titans of the digital age: Facebook and Google.
To complete this complex con job, Rimasauskas and his wiseguy goons set up a fake company registered in Latvia, with a functioning website, lookalike domains, email addresses, and even bank accounts – all the dressings required to pass as Taiwan-based parts manufacturer, Quanta, who was actively working with the two companies at the time.
Rimasauskas designed sophisticated phishing emails, uniquely tailored to specific Google and Facebook employees, invoicing them for true goods and services that Quanta had actually provided to the tech giants, implying that payment had yet to be made.
Massive amounts of money were deposited via wire transfer into the many fraudulent accounts Rimasauskas had created, spread across Latvia, Cyprus, Slovakia, Lithuania, Hungary, and Hong Kong, while he quietly sat behind a computer halfway across the globe.

When he was caught before Christmas 2016, Rimasauskas had barely even touched the money – he was just the guy asking for it (or so he said). He owned up to the charges, pleading guilty to fraud through a Russian translator in a Manhattan court after his extradition to the states. He got 60 months in the American slammer (I’m bringing that term back), in addition to forfeiting $49,738,559.41 in illicit dividends, and paying restitution in the amount of $26,479,079.24 to two already very rich tech corporations.
It might be tempting to savor the schadenfreude of giant, ad-spamming, data-farming corporations getting a bit of comeuppance - but the truth is this could have just as easily targeted small businesses and ruined people’s lives.
While Rimasauskas had a complex and elaborate system in play here, simple phishing scams remain a problem for everyone on a much smaller scale. Security firm Aurora claims losses from identity theft cases totalled $502.5 billion in 2019 and were expected to rise 42 percent to $712.4 billion in 2020, with further increases expected each year going forward. In short: identity theft is not going away.
So What Can We Do About It?
My colleague and favorite cyborg, Database, wrote a great article about how to minimize threats to your privacy and information that you should read in all of its glory here. While you deep dive on internet security, here are some simple tricks to tide you over:
1. Use Strong Passwords/Try a Trusted Password Manager
In order to best protect yourself, you shouldn’t use anything in your password that someone could identify you with, from birthdays to phone numbers to pets names. Mix up the letters and numbers, add symbols, and use a combination of upper and lowercase letters whenever possible. Most of all, don’t ever recycle your passwords; new and unique passwords only please and thanks!
2. Look for Encryption (HTTPS vs HTTP)
Look for the trusted security lock symbols in the address bar, and the extra “s” at the end of “http” in the URL. Before you make any purchases or divulge information, make sure your connection is secure. Using Windscribe here is also a great idea!
3. Turn on Web Browser Blacklisting
Many web browsers have additional security options, like blacklisting. This allows you to set the criteria for sites you will be navigating; only secure, trusted sites will be available to visit. You can also do this through your R.O.B.E.R.T. settings in Windscribe to further customize your browsing.
4. Avoid Phishing Scams
At this point, we should all know never to open emails or attachments from persons unknown, and certainly don’t click on unsecure links in said emails. Hover over hyperlinks and see if they go where they say they do, whilst watching for simple spelling and grammar errors throughout the email. No donations from foreign princes, either!
5. Hide Your Personal Information (AKA Use a VPN)
Check your browser settings when you set it up and make sure you only allow sharing of the info you want. Watch what is being stored via cookies - and don’t be afraid to say NO to them (or yes to Windscribe’s Cookie Monster). Always use your Windscribe VPN, especially on public networks, and only give the information you must to those you trust!





