Learning how to keep yourself more private & secure, whether online or in-person, is a daunting task. The definition of privacy is not universal, and keeping up with all the latest information is very tricky - but, unbeknownst to the Tech Gods, you're a Windscribe blog reader, and we're here to help!
In this article, I take a look at the What and Why of threat modelling, how it affects the privacy community, and I design a basic entry model and give some suggestions on additional steps you can take. So settle in, grab your caffeinated drink of choice, and get ready to dive into the wide world of threat modelling with me!
The What and Why
For those unaware of what it is, a "threat model" structures information on threats that can affect the security and privacy of an individual, business, or application, and how to combat them. When designing a threat model, it is standard practice to highlight assumptions, potential weaknesses, and actions to take, and then verify any actions taken.
A threat model often has layers pertaining to individual topics that are assigned certain levels of importance. A common example would be:
- Accounts
- Payments
- Software
- Data
In the ever-growing tech world, data breaches and privacy violations are becoming the norm, and without threat modelling, we'd be as lost as a GPS system in a polar reversal; we simply would not be aware of everything that's out there, nor be able to take the necessary steps to protect against attacks we are concerned about.
Designing a threat model lets you methodically outline what potential security breaches are most important to you, and list the actions you will take to remedy them. It lets you make sure you've covered all bases, and lets you have a checklist so you can be sure you've taken all the necessary steps. That's why, when we are looking to improve our privacy, a threat model is the first thing we do.
Ignore the Gatekeepers
Before we get into the nitty gritty, we need to address a major topic: gatekeeping in the privacy community. There are a handful of people in the community who believe that their threat model is the only correct one, and they'll try to convert you to their way of thinking so fervently that you'll be hearing “WOLOLO” in your dreams. You'll be told a wide range of things, including to use Tor 100% of the time, to delete all of your accounts, that X is compromised so use Y (often this isn't even true), or even to just destroy your device. If you don't take their advice, you'll be told you're not serious about privacy. Don't believe me? Join a privacy-based Discord server or subreddit and ask an innocent question about making Windows or Google or something more private and secure, then see how it goes.
If you know what's best for you, you'll ignore these people. They can be very convincing, using rhetoric, buzzwords, and bull-headed confidence to try and convert you, but their beliefs are theirs, and are not necessarily even accurate, let alone indicative of what will work for you.
Fortunately, as with most communities, the small number of dickheads are exactly that: small in number. Most people in the privacy community are friendly and helpful, and you will be able to find a useful and accurate answer to any of your questions and concerns. Don't let the idiots make you feel unwelcome!
Setting a Goal & Expectations

The first step to achieving your goal is figuring out just exactly what that is. You need to take the time to really think about what it is you're looking for, and what your expectations are. Things to ask yourself include:
- Am I looking to protect myself from individuals, corporations, governments, or all three?
- How many hoops am I willing to jump through to meet my standards?
- Will what I'm looking for require drastic changes to my workflow, such as deleting my Google, Microsoft, or other accounts?
- Will I still use proprietary software, or am I aiming for all open-source software?
- Do I trust a specific service with a majority of my data if they promise to protect it?
- Are there certain practices that are better than others?
These are some commonly asked questions among those looking to get started, but don't stop there! Do some research on what's taking place in the world regarding your privacy & data, and decide whether it's something you'd like to avoid, or that you don't mind all that much.
In addition, set a timeframe for when you'd like to transition into your goals. I know some like to bite the bullet and get started immediately, and if that's what you want then that's totally fine! If, however, you require some time to think about it or to put your plans into action, set a time goal with occasional check-ins on your progress. Something like this:
3 months from now, I intend to implement my plans, including privacy controls on my existing accounts and deleting old or unused ones, switching away from Gmail to Tutanota, controlling Windows privacy, and exploring Linux as an option for a daily driver.
Having your goal(s) laid out will greatly help you achieve them. Do what works for you, and set goals that you think you will be able to achieve in a reasonable timeframe.
Acting on the Model
So you've got your expectations and goals set; now, it's time to act. It is important to find a good balance when it comes to how much effort you want to put into certain tasks. I suggest starting with what you think would be the easiest for you to implement and requires the least amount of changes, and then progress into more of the bigger stuff once you've got your feet wet. Here are a few tips for when you begin actioning your model:
- Keeping a list of what to do in a document or even a whiteboard can help in organizing what to do next (but if you do things another way that is totally fine)
- Don't be afraid to revisit your model and decide if something isn't going to work right now, or is no longer relevant at all
- Whenever you successfully action one of your goals, reward yourself for a job well done to keep that confidence going!
- If you're struggling, or find yourself straying, keep reminding yourself that you're doing this to improve your privacy, and have a happier, freer online life
Examples of Threat Models
There are many levels to privacy; maybe you're just looking to make your existing accounts more private, or maybe you want to go balls to the wall with Tor and Qubes behind 9 proxies after moving to a remote island in the Pacific. Not to worry, we'll go through each of them. Cherry-picking topics and deciding for yourself is expected, as you may, for instance, care about mobile privacy but not much else.
Newbie's First Threat Model

Let's start with catering to more fresh-minded people that want to put some control back into their hands, and don't need to drastically change their arsenal to feel like they have achieved something. People often forget, but there are indeed ways to make even a Google account more private!
So let's establish our goal, and break down the different areas we want to make some simple and effective changes to our privacy.
Goal
To get back some control over my data while using mainstream applications
Privacy Control
Google, Twitter, and Microsoft are some of the biggest data farmers, and I use their services. I will immediately go to the privacy settings on any of these apps, turn off any tracking options, and deny any tracking requests.
Account Cleanup
I have signed up for many accounts over the years that are likely still there, containing my data. I will immediately delete my Narwhal fanfiction account from years ago, and then sift through my e-mails to track down any more. If an account is proving difficult to delete, then I will alter the information to nonsense.
Trackers
Trackers are everywhere on the internet, and I want to control them. Chrome is notorious for providing no protection. I will immediately download, install, and make the switch to the Brave browser, and install the uBlock Origin extension to give me a starter level of protection.
Within 1 month, I will have signed up for a trustworthy VPN service with DNS-level ad and tracker blocking, and that doesn't riddle their own site with trackers. Windscribe, Mullvad, and IVPN all look promising.
Payments
I want to limit the number of sites that collect my payment information. I will immediately purchase some Visa Gift Cards to use as prepaid options.
As some sites don't accept prepaid options, within 1 month, I will look into using Privacy.com or Revolut to generate per-merchant virtual cards.
Levelling Up Your Privacy
Maybe you want to go a step further than a basic model - maybe you've had enough of these services that don't respect your privacy, and want to cut them out completely.
First, consider replacing commonly used services with ones that have a better track record of respecting privacy, like the following:
- Google Search -> Startpage/Brave Search/Kagi
- Gmail -> ProtonMail/Tutanota
- Google Docs -> Skiff
- Discord -> Matrix
- WhatsApp -> Signal
Then, for services you simply cannot live without, consider alternative "frontends". They come tracker-free, VPN/Tor friendly, open source, and extremely lightweight. There are many and we'd be here all day going through them all, however I will highlight a few I enjoy.
- YouTube: Piped - supports subscriptions, up to 8K playback, proxied by default, no ads, and SponsorBlock integration. Android - NewPipe, iOS - Yattee (AltStore or TestFlight needed)
- Reddit: Libreddit - since I'm one of the only people on Earth that prefer the new design of Reddit, or Teddit if you prefer the old design. Lightweight and everything proxied
- Apple Music: Cider - does what Apple themselves won't, which is give Windows and Linux a proper desktop app. 1000 times better than using the web version and it's all open-source
- Honorable mentions: Nitter (Twitter), Bibliogram (Instagram), and ProxiTok (TikTok)
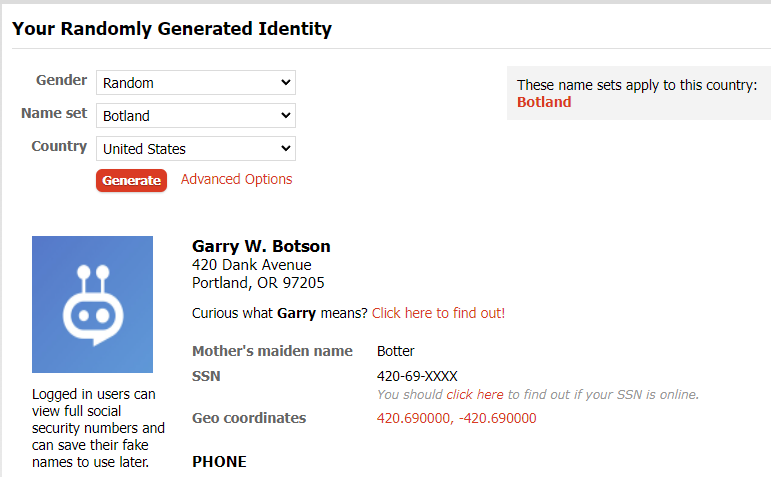
Next, look at pseudonymous / anonymous methods of registration and payment.
- Tools like Fake Name Generator will randomly generate fictitious info, and if a portrait is required, This Person Does Not Exist can generate realistic images. Temporary emails like Temp-Mail and/or alias services like AnonAddy or SimpleLogin are great to keep things out of your main inbox.
- Cryptocurrency, if accepted, is preferred. By using it you cut financial institutions out of the picture, which prevents them from collecting and selling your financial data. Monero is the best choice for anonymity right now, however there are still private ways to get other currencies like Bitcoin. Look at local exchanges like LocalBitcoins or LocalMonero, Bitcoin ATM's, or non-KYC exchanges. Disclaimer: Use all financial services at your own risk.
- Maintain the separation of your pseudonym. Under no circumstance should you do anything that links your real identity to your alias.
It's also important to consider that a VPN should not be the only thing in your arsenal. Consider starting to use Tor for some things. While Tor is widely known for (cue ominous music) "the dark web!!!!", it is fundamentally an anonymity protocol that breaks surveillance and censorship. It is useful to use for general browsing, but remember not to sign in to anything or install extensions, as that will defeat the purpose!
Do keep in mind the additional protections of Tor make it considerably slow by design, so don't expect to be streaming in 4K on it.
Finally, consider running something like Linux on your PC, installing ROMs like CalyxOS and GrapheneOS on your Android devices to strip Google's control, and sticking to open-source software wherever possible.
Min/Maxing

Finally, for some people, even the above options are not enough; there are eyes everywhere, they all want your information, and if you don't act now, they're going to get you!
We're talking exclusively browsing the web using Tor, loaded on a Qubes OS device with maximum security settings, refusing to use anything that isn't open-source, deleting all accounts to remove every bit of trace you can from the web, and burning all your electronic devices to go live in an Amish Paradise.
Okay, that last one is a bit hyperbolic, but the point is you can go hard on your privacy and security lockdowns if you want to - though I'd recommend maybe just starting with the basics!
Keeping On Top
Most people when they are taking their first steps to control their privacy on the internet do so with the intent to control what kind of profiling and marketing data various entities gather on them; essentially, they want to block ads and trackers. After setting this up, it can be tempting to think you're secure, and no more work needs to be done, but without a threat model that stays on top of the latest developments in the security & privacy world, there are consequences that go beyond the ads you see. Don't believe me? Take a look at the thousands of companies that have suffered a data breach, and all of these recent privacy blunders.
Without a threat model, you won't be aware of which companies have good privacy records in the first place, but it's also important to realize that your threat model may need to change over time based on the rapidly advancing field. It's likely there will come a time when a certain service becomes compromised, can no longer be trusted, or is simply behind the ever-advancing curve on data security; if that's the case, you have to be prepared to make changes and find alternatives. It might not be a cakewalk, but it's important if you don't want any holes in your ship.
Go Get 'Em
In closing, remember that everyone is different, and you don't have to follow the example above to the letter; there is way too much info to cover this topic in its entirety, so this article is just intended to introduce you to threat models, and get you started on your path to a safer internet experience. Research and personal desires are key to making your ideal threat model, so get out there, and get tackling those threats!

