Allow me, dear readers, to take you through a tale that has it all - confusion, scandal, humor, (almost) termination of employment, and a lesson on internet privacy.
After a particularly hectic day at work at a previous job, I found myself with some time to kill and with a fast internet connection at my disposal; I couldn’t contain my excitement and had a ball of a time to myself! I was quite puzzled, however, when I was called in by the HR Director the next day.
“Kailash, we’re all for our lovely employees unwinding after work, but there are certain things that are unacceptable at any workplace - even one as laid back as ours!” they said. What on Earth were they on about? I merely checked my socials, video called a friend, and watched an educational Math video.
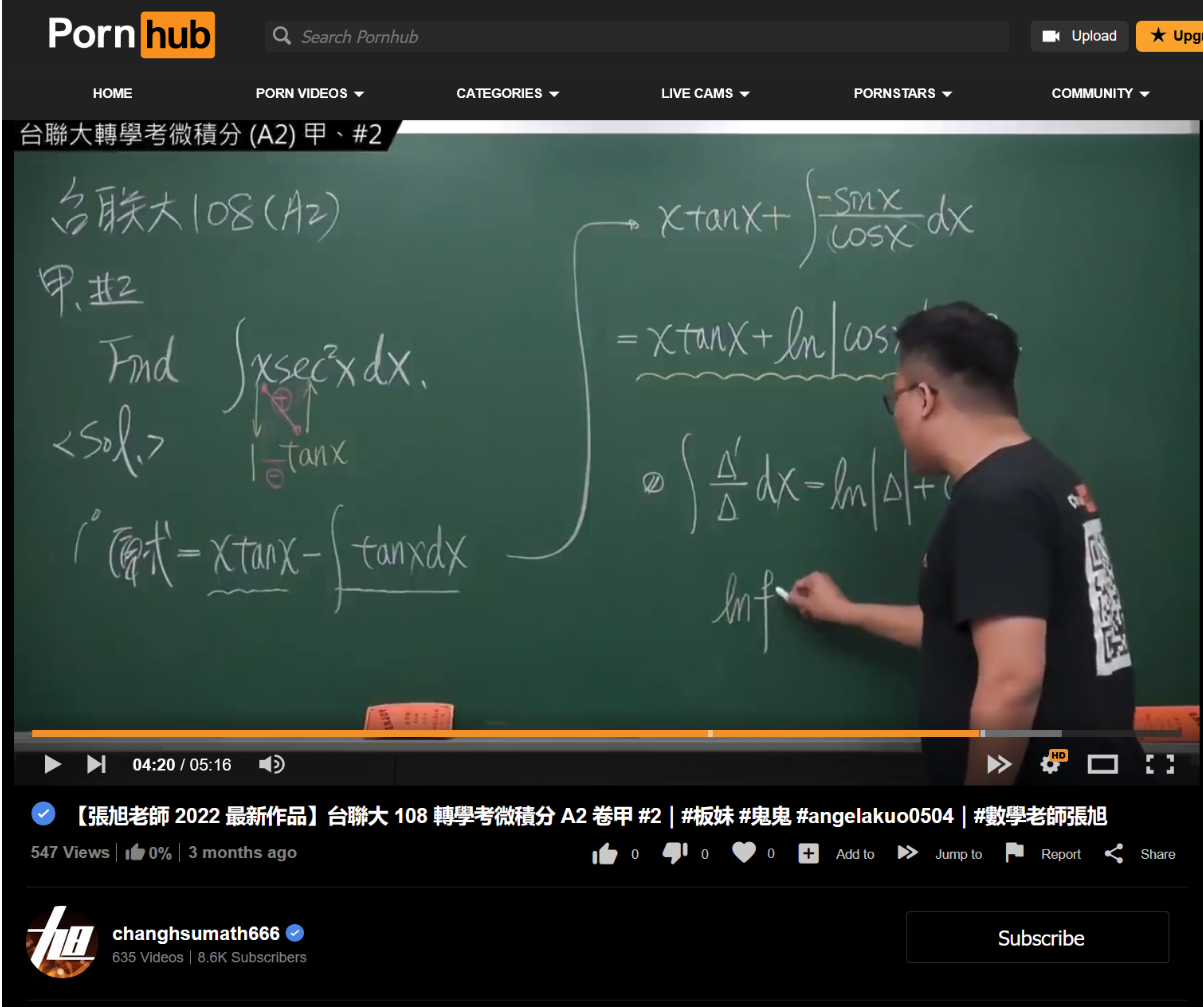
I fail to see what’s scandalous about indulging in some calculus whilst at work, but oh sure, HR chooses to see I visited “https://www.pornhub.com/”, and gets all premature on me (I'm sorry, I won't do that again). Looks like HTTPS has been a fly in the ointment in an otherwise perfect unwind session at work! For once, I had hoped my employers would see the entire URL (with the actual resource, not just the domain name).
This incident got me thinking - what can a network administrator (be it at school, or public places like a coffee shop) see when I’m on their network?
Let’s try and see for ourselves with WireShark, a packet analysis tool.
Going In Without a VPN
What happens when one decides not to use protection? Perhaps people who do this are just dabbling with exhibitionism? (I swear, I'll stop).
HTTP traffic
When I visit the world’s first website, http://info.cern.ch/hypertext/WWW/TheProject.html, my ISP / employer can see:
- Exactly what server I connected to (in this case, the server’s IP address was 188.184.21.108)
- The “host” (or what website I was browsing)
- What resource / page I accessed on the website (in this case, /hypertext/WWW/TheProject.html/)
- What the contents of the above resource are
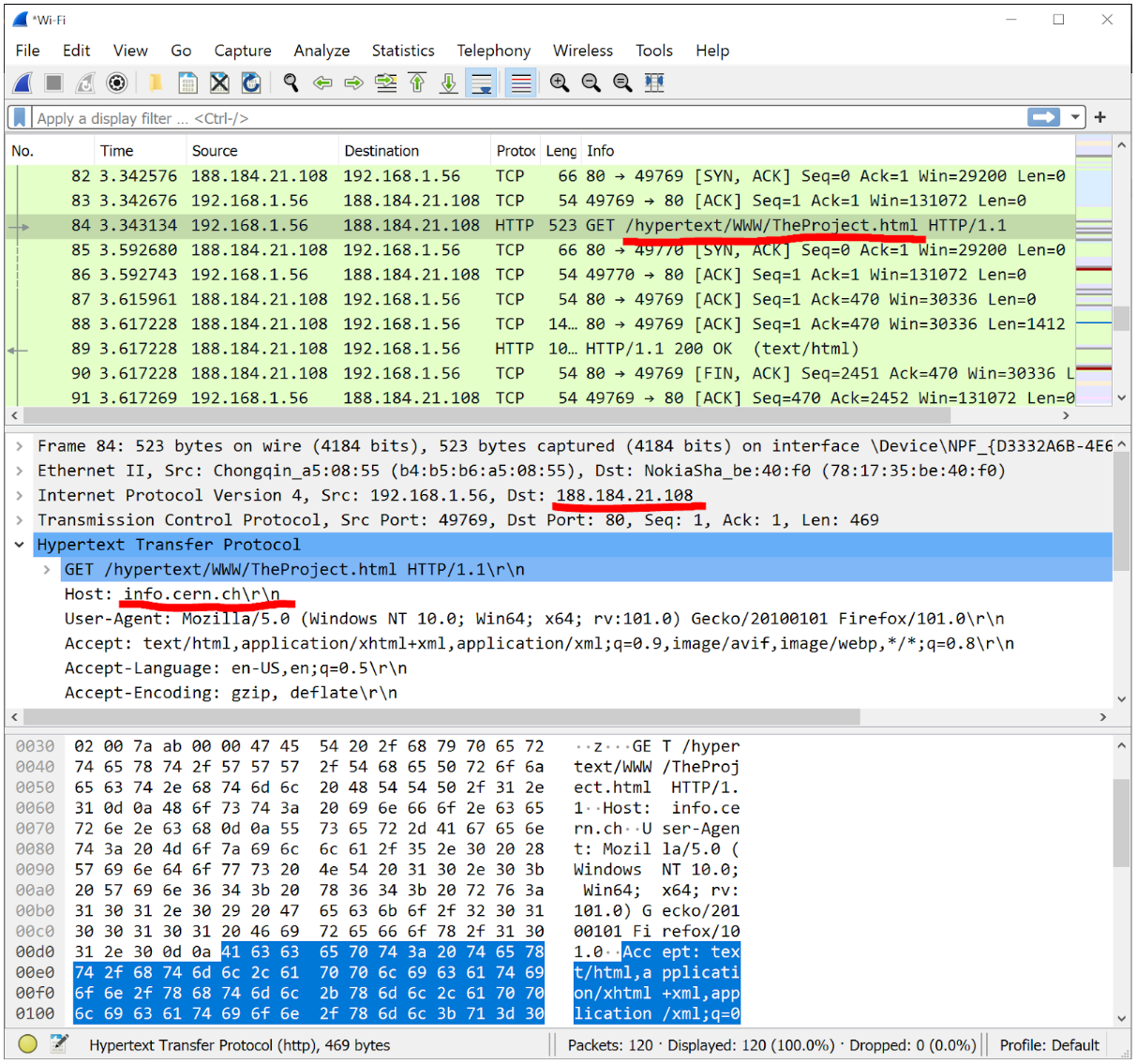
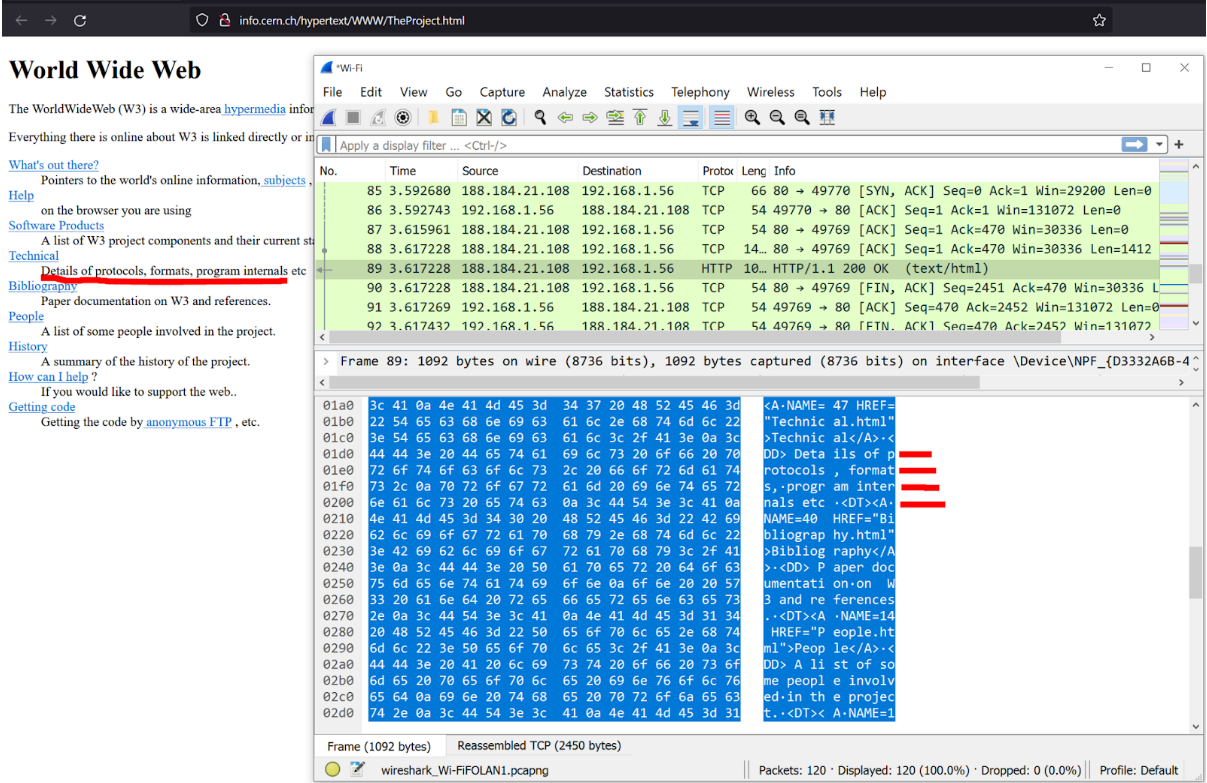
This is worst possible case and is about as exposed as one can get online. Fret not, though, since there has been a concerted effort to phase HTTP out. HTTPS has become the norm now, and sites not using HTTPS are expressly marked “not secure” by most browsers these days.
HTTPS traffic
When I visit a website using HTTPS, say https://home.web.cern.ch/, my ISP / employer can see:
- The destination of the packets (where I’m requesting data from). In this case, my ISP / employer will see that I’m making requests to receive data from the IP address 188.185.88.30, which belongs to CERN
But not:
- Exactly which resource I was looking at
- What the contents of that resource are
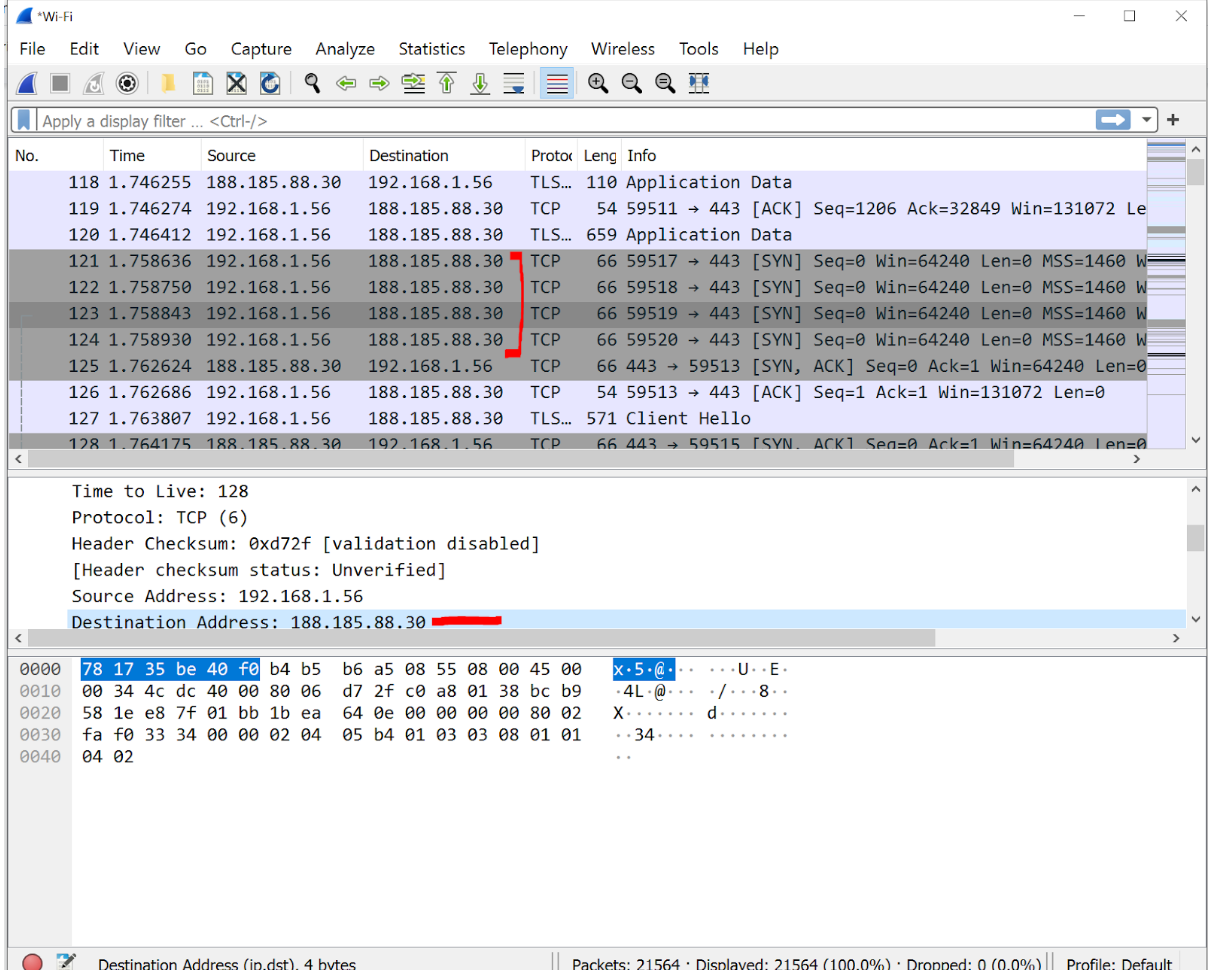
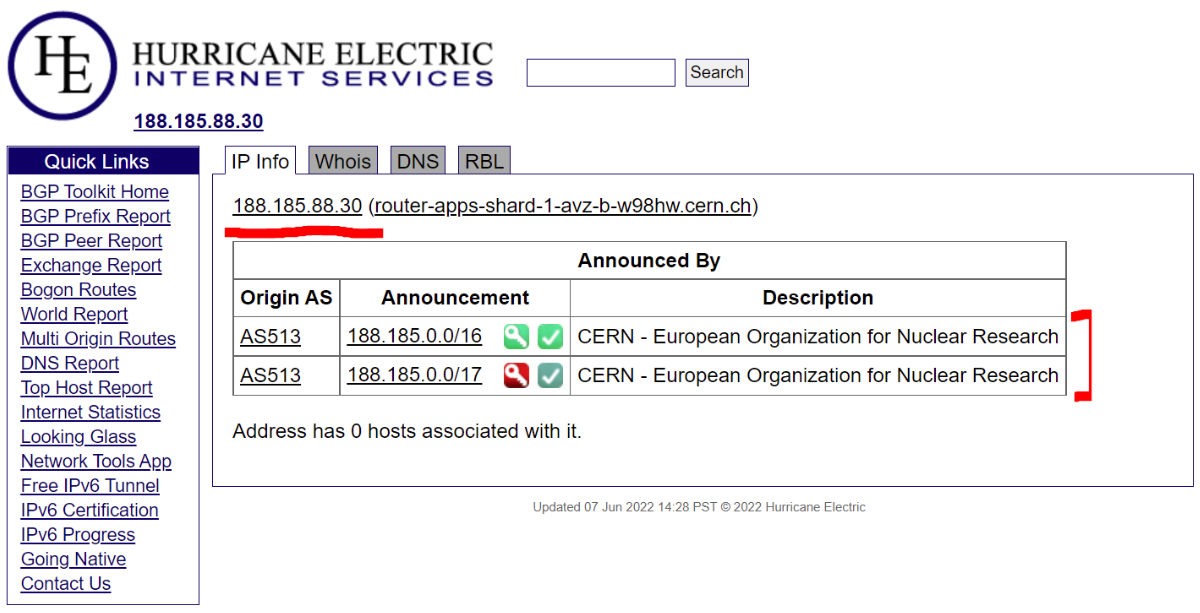
Better, but not ideal - seeing as how the domain name may either be a dead giveaway (No mystery what I might be doing on https://www.cat-lovers-only.com/) or, as I found out, cause confusion due to missing context.
(Legacy) DNS Traffic
Your ISP / employer can get a really good idea of what you’re surfing and what apps are on your device.
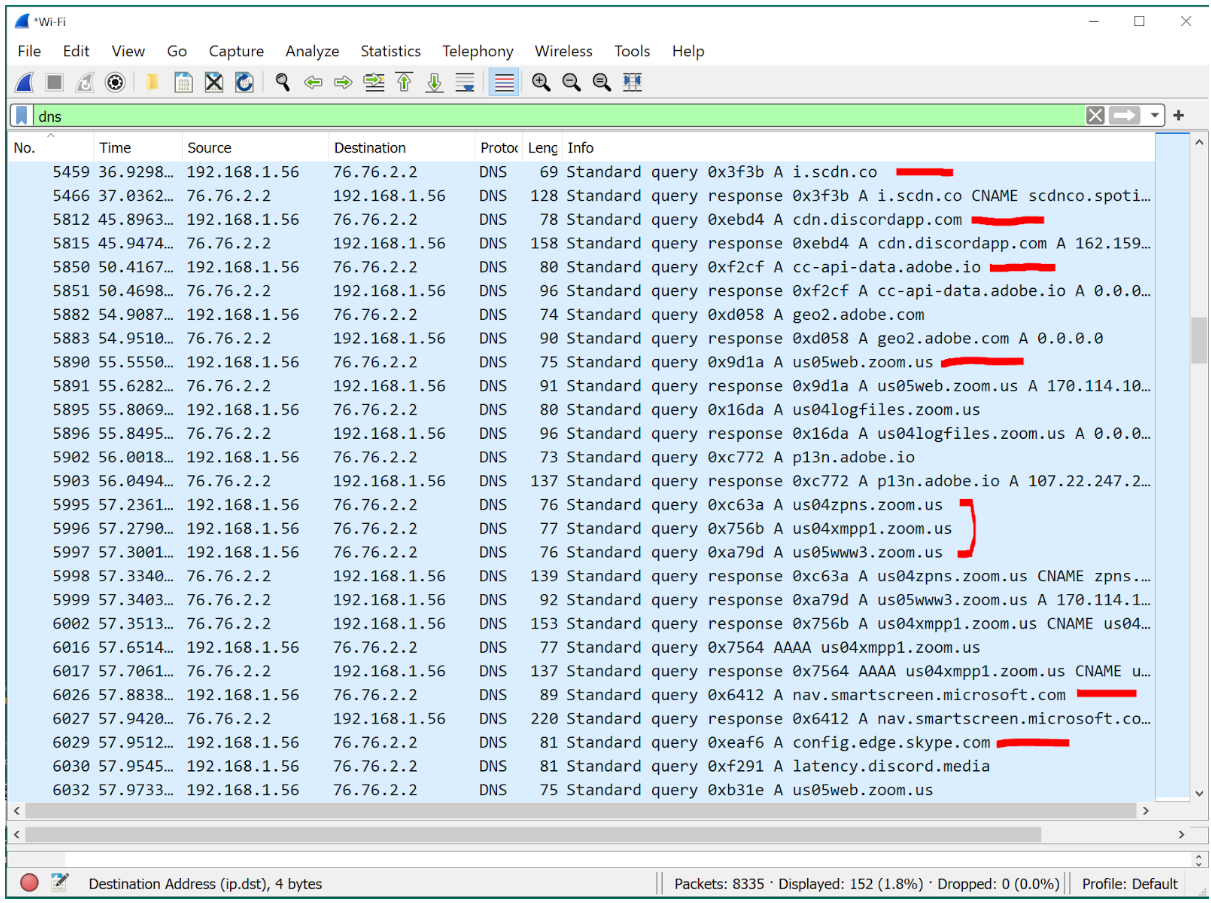
While DoH (DNS-over-HTTPS) takes it a step forward by encapsulating DNS requests in HTTPS packets, one’s ISP / employer is still able to observe the SNI (Server Name Indication) header, potentially figuring out the destination of the packets. ECH (Encrypted Client Hello) looks to mitigate this problem.
Pretty creepy if you ask me! Let’s see what one can see with a VPN in place.
VPNs: The Durex of Internet Security
(Alright, fine, I'll show myself out.)
All the ISP / employer sees is the VPN server’s entry IP address. They know which server the user was connected to, but they do not see what the user was up to whilst connected. Law enforcement authorities may attempt to subpoena the VPN provider to hand over this information, but a no-logging VPN (like Windscribe) will have nothing useful to share.
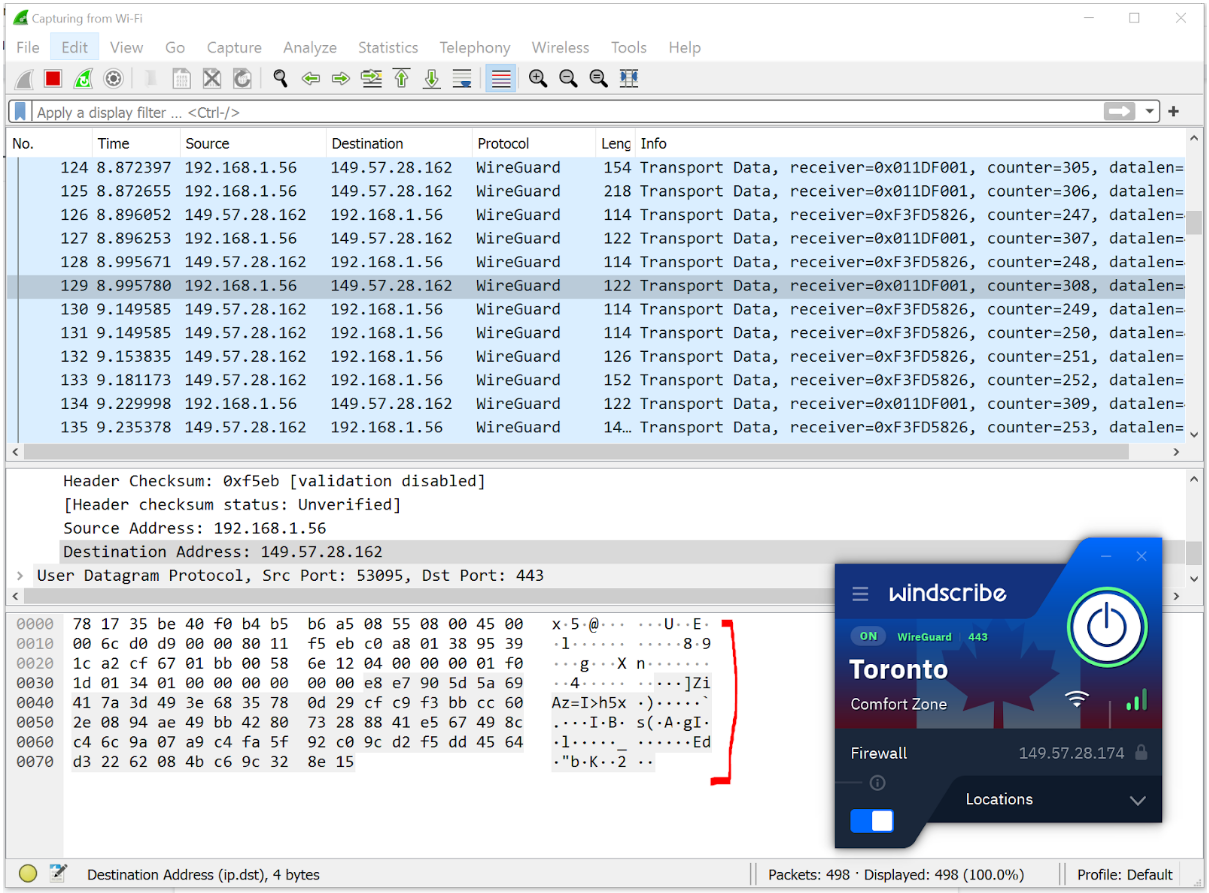
All the provider can see is gibberish (it only makes sense to the VPN server - which decrypts this traffic using the private key).
Wrapping It Up
(Okay, look, I'm literally showing myself out the door.)
Fortunately for me, I didn't end up losing my job over this - but I did learn a few things from it. Allow me then, dear reader, to summarise some of those lessons for you. Find a giggle in my stupidity, and know what I wished I knew sooner:
Without a VPN, network administrators can monitor:
- A lot about HTTP traffic: destination of the packets (host’s IP address), the host itself (the address of the website), address of the resource, and the actual content of the resource
- A fair bit about HTTPS traffic: destination of the packets (host’s IP address), and the host itself (the address of the website). This may still give one a good understanding of what one is up to due to context, or may cause misunderstandings due to lack of context
- DNS requests will give up a great understanding of what sort of applications are running on your device. Legacy DNS requests are unencrypted. Using DoH is useful to an extent, but a sufficiently motivated adversary may still figure out the nature of traffic from the SNI header
Whilst connected to a VPN:
- All the snooper will see is the entry IP of the VPN server and at what times you were connected to it. All traffic will appear to be gibberish to anybody looking in the chain of networks between you and the VPN server. It makes sense exclusively to the VPN server itself, which decrypts this data using the private key
- A no-logging VPN will have nothing useful to share to anybody that requests it - even when we are legally obligated to answer - since we legally operate a no-logging VPN service
And most importantly, I should have a VPN installed like Windscribe so that my HR Chief can't misunderstand what I'm doing, and doesn't give me a hard ti-... come down on m-... bust my ba- alright, yeah, I'm just leaving.