One of our principle goals at Windscribe is to create innovative features to enhance our users' online privacy. We spend a lot of time interacting with our userbase to ensure that we are building software that our users actually want (and in many cases need). And so was born our latest feature: Decoy Traffic Mode. Now available on the Windscribe Android app, Decoy Traffic Mode helps combat traffic correlation attacks on adversarial networks, making it considerably more difficult for threat actors to identify you online.
What is a Traffic Correlation Attack?
When you use the internet, regardless of whether you are using a VPN, your device does two things:
- Uploads data
- Downloads data
Uploading data is when your device emits packets to a remote server, and downloading data is the reverse. Almost every single tap of every single button online involves uploading and downloading.
When you use a VPN, the packets transmitted to/from your device to a VPN server are encrypted, so an outside observer (network administrator, ISP, government) cannot tell what the data is or what you're doing. This is great, but there is one thing that you cannot hide - how much data is being uploaded or downloaded from from your device.
Here is what browsing Twitter for 5 minutes looks like. To a network administrator, this graph would look identical, regardless of you using a VPN or not.
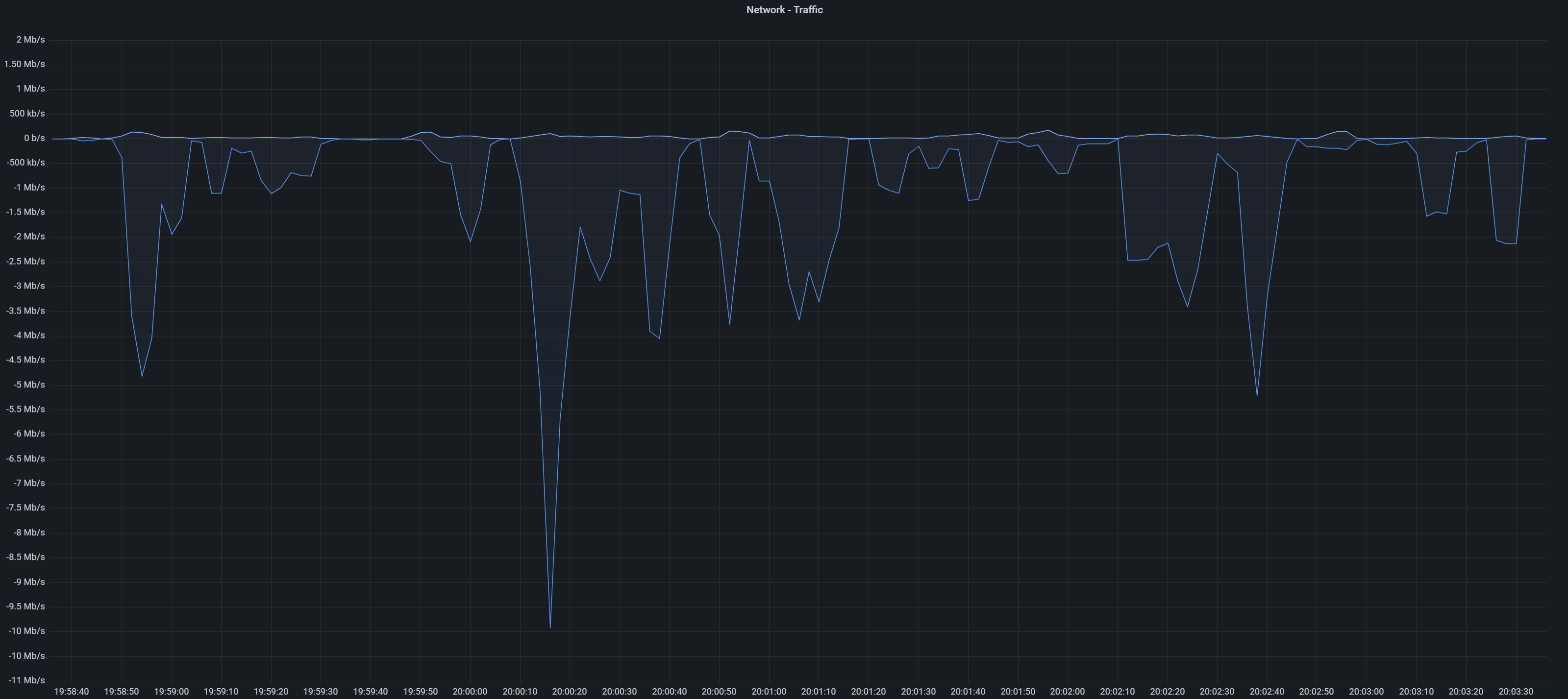
This graph basically shows the throughput of your uploads (top graph) and downloads (bottom graph). When you browse Twitter, you mostly download things like text, images, videos, etc, which is why most of the activity is on the "download" side. This is what a typical user's traffic pattern looks like.
Here is a more topical example - uploading a 50MB file to a Telegram channel.
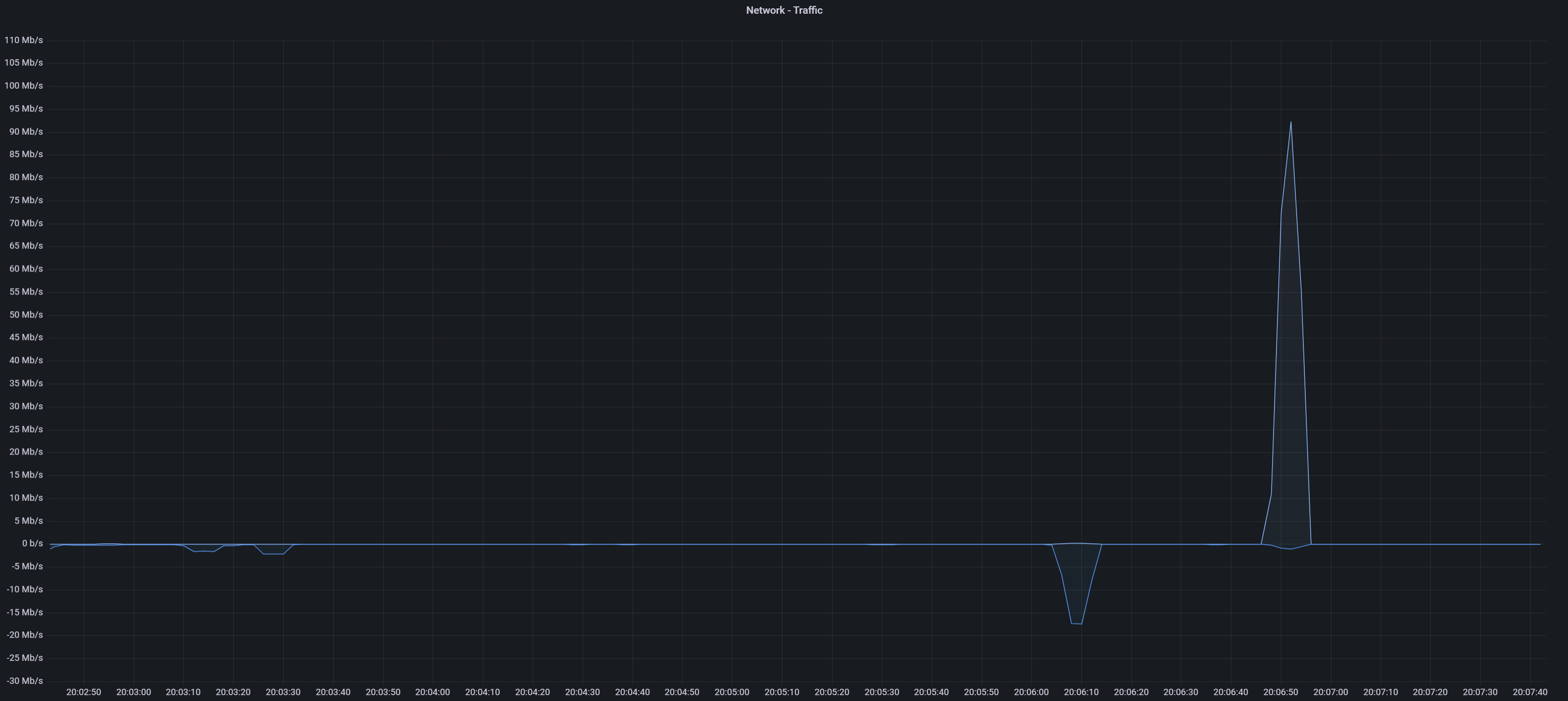
Notice the huge upload spike (top side of the graph); this is the 50MB file being uploaded from your device to a remote Telegram server.
So, you may be thinking: "Cool graphs, why do I care?". If the following applies to you, then you should pay close attention:
- You live in an oppressive country with no freedom of speech
- You post anti-governmental material on social media (Twitter, Telegram, etc)
- You leak sensitive material that someone would be upset about
How to Catch a Dissident
People living in oppressive regimes who use social media to upload content that the local government deems "bad" are at constant risk of being identified, located, and arrested. For this reason, most dissidents use VPNs in order to mask their IP address so the government cannot directly trace their location. Whilst this helps and is crucial in the short term, it will unfortunately not prevent you from getting caught if you are an active dissident over a prolonged period of time. How do the governments do it? It goes something like this:
- You upload a sensitive 50MB video or document to social media at 12:30 pm
- The government goes to local cellular provider(s) and asks them: "Which subscribers uploaded at least 50MB of data at this exact moment?"
- This will yield a large set of customers, since phones are constantly uploading and downloading things, even without your actions
- They will then watch the Telegram channel for more posts over some period of time and capture groups of customers that uploaded x MB of data at the exact moment of those posts
- They will analyze the traffic logs/graphs (like the ones above) for large upload spikes. Since 90%+ of average person's data usage is downloading, large file uploads stick out like a sore thumb. They're very easy to spot.
- After a while, they will be able to identify a single customer that has these upload spikes at the exact moments of posts being made on social media
- They then have what they need to find and arrest you
Whilst it is more difficult to execute if you are using a VPN or Tor, this type of attack is still well within the realms of possibility.
Decoy Traffic
This a new feature currently available in the Windscribe Android app. In a nutshell, it does the following:
- Generates large amounts of fake traffic between your device and the VPN server
- Throttles your connection
Point #1 creates a lot of random "network noise" and attempts to hide the upload of sensitive content in the midst of all the fake activity generated by the Windscribe app. It creates random upload (and download) spikes, so when you happen to upload some sensitive material, it looks indistinguishable from the activity that came before, during, and after the upload.
Point #2 throttles your connection in order for the upload to be much slower than what most LTE and 5G networks are capable of (100+ mbit). The idea is to reduce the magnitude of the "traffic spike" and have the upload take as much time as possible. The longer the upload takes, the bigger chunk of time the adversary will have to look at when they're asking the ISP for "Who uploaded 50MB at this time". The bigger the time window, the more useless the dataset will be, and the harder it is to single out an individual customer. Here is what uploading the same file to Telegram looks like when Decoy Traffic mode is enabled.
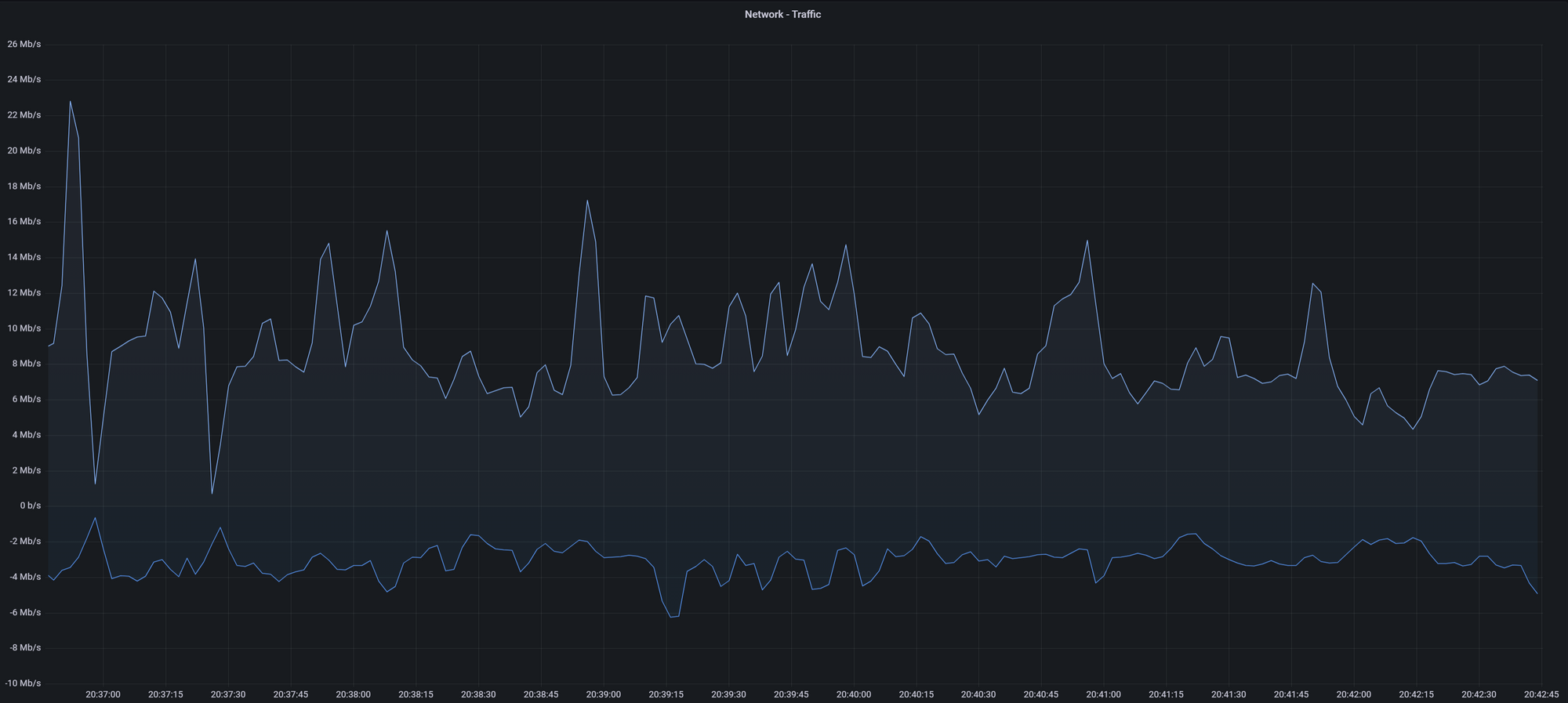
Can you tell where the upload happened? Right in between 20:37:30 and 20:41:45. No upload spike, because the upload took almost 10x longer than it normally would, and your device transferred a LOT more data than 50MB. This graph could easily represent a video call, or some other bandwidth intensive use case.
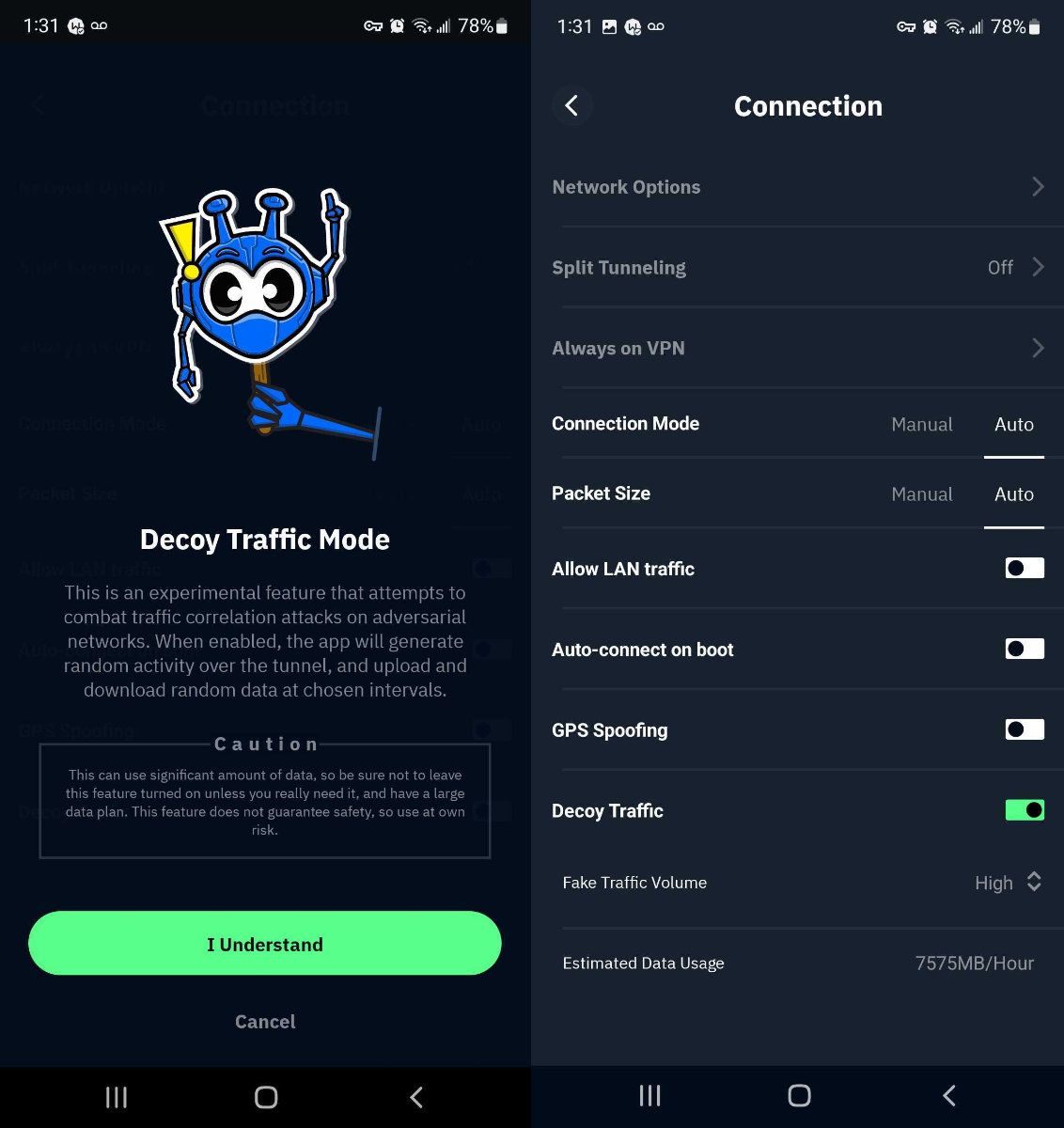
How to Enable Decoy Traffic Mode
You will need the Windscribe Android app version 3.1.883 or newer to use this feature. To enable, go to Preferences -> Connection tab and toggle the Decoy Traffic switch. Then choose one of the 3 levels:
- High - most secure, but will use the most data
- Medium - will use less data, but is less secure
- Low - will use the least data, but is least secure
You will see estimated data usage per hour for each of those modes.
A Word of Caution
This is an experimental feature, and you should not bet your life on it. Oppressive governments that resort to this type of thing aren't exactly keen on sharing how they catch dissidents; the method outlined above is a no brainer, but they could also have other methods up their sleeve. By it's very nature, it's also impossible to gauge the effectiveness of this mitigation, since we can't exactly A/B test it, or get any type of feedback on the success of this feature.
If you're already posting content that your government may frown upon, using this feature will improve your chances of staying safe, but don't consider this a carte blanche to engage in risky behavior with no fear of retribution. There is no such thing as 100% safe.
Finally, when this feature is enabled, it will generate a LOT of fake traffic. Think gigabytes. If you're on a limited data plan, it can chew though your entire bandwidth allowance in a matter of minutes/hours. So use it responsibly. If you will be using Decoy Traffic Mode often, we recommend you upgrade to our Pro plan as it provides you with unlimited bandwidth.






