Here at Windscribe, we’re always thinking about the next big thing and what the future holds. How will AI shape the fabric of human society, what happens in the post-quantum world, what is a reasonable amount of platypuses one can own without being called a crazy person? We don’t know the answer to the first 1 question, but the last one is a hard zero. The 2nd one will be addressed later.
As you’re aware, Windscribe is a VPN provider (a damn good one if you ask me). At the core of any VPN service are the VPN servers that you actually connect to in order to change your IP address. When you connect to a VPN server, it establishes a VPN “tunnel”, which looks like this:

You can clearly see the tunnel engineers patching holes so the encrypted packets don’t leak out. If you haven’t caught on yet, this is a poor attempt at humor. What you’re actually looking at is the Wendelstein 7-X nuclear fusion research reactor. But in reality, these “tunnels” are established by off the shelf VPN software, such as OpenVPN and StrongSwan (IPSec/IKEv2). Each piece of software speaks a different “language”, also known as the protocol.
Windscribe uses the above 2 applications to provide VPN tunnels to all our VPN server. These protocols and applications have existed for well over a decade, and are massive code bases written by dozens if not hundreds of people. They are meant to support many use cases, most of them not applicable to a privacy oriented VPN service. They also have a lot of overhead, which may slow down the connection in some cases.
What is WireGuard?
WireGuard® (is a registered trademark of Jason A. Donenfeld) is yet another VPN protocol which came into the scene in 2016, but was not widely used until 2019. It’s advantages include:
- Small code base — few features, less chances for things to go wrong.
- Theoretically high speed — the protocol is implemented in kernel space, which allows the OS to do the heavy lifting. Under ideal network conditions, this will yield better speeds than all other protocols.
- Fast connections — Unlike other protocols, there is no “connecting” phase. It either works, or doesn’t. This allows for nearly instant connections to VPN servers.
The disadvantages include:
- Few features — any advanced behavior has to be created from scratch, outside of the protocol. This is mandatory for a commercial operator like Windscribe.
- Not privacy oriented — Steps have to be taken in order to secure it for the commercial VPN use case.
- Assembly required — For anything other than a simple or internal-only deployment, you cannot operate it out of the box. Additional supporting software must be created for large deployments.
What we did
We’ve tested several implementations of the WireGuard protocol, which include:
- DKMS kernel version — the fastest
- Boringtun — good enough
- Wireguard-go — the slowest
Although the DKMS version does indeed offer the fastest throughput over the tunnel in an ideal scenario, these gains will not be realized for vast majority of users (everyone who is not running Linux on a 10Gbit connection). Every other platform will use the user space implementation (Wireguard-go), so that will be your bottleneck. Additionally, modifying kernel modules is rarely a good idea, and even if you did, you’re still limited in what you can actually do behind the scenes which makes it impractical for Windscribe, that must support 20M+ users.
This is why we chose to use Boringtun, which is a Cloudflare implementation of the WireGuard protocol in Rust programming language. This gave us several advantages:
- Easy to modify — We modified the software to suit our specific requirements and needs. See below.
- Easy to deploy — Download a compiled binary and run it.
Remote Authentication
When you connect to a WireGuard server, your public key must be known to the server. It is not practical to deploy 20M+ keys to every server we operate. Instead, we modified Boringtun to pull this data from a remote source, similar to how all our other protocols work. The remote data source tells Boringtun if this connection is allowed (account is in good standing, and can access this specific server), what IP address should be assigned, and what the user’s pre-shared secret is for additional security.
Post-Quantum Resistance
As far as we know at the time of writing, no other VPN provider supports pre-shared keys when connecting over WireGuard. When you use WireGuard with Windscribe, we generate a unique pre-shared key for every user. This is used in addition to the standard public/private keys that WireGuard relies on to work. This functions as an additional layer of security that makes these tunnels “quantum resistant”, meaning that even if you cracked the keys on a hypothetical quantum computer that may exist in the future, you still would not be able to decrypt the traffic.
Traffic Accounting
Since Windscribe is a freemium service, we need to know the byte count of how much data was transferred so we can enforce free tier limitations, prevent abuse, and ask you for money when you run out of your free data. This modification creates a basic json API that allows us to extract these byte counts (that WireGuard keeps anyway) and increment counters on our end.
Hide The Source IP
By default, WireGuard outputs the endpoint IP address when you run the utility. The endpoint IP address is your actual IP address, since that’s required to be known to WireGuard for it to actually work.
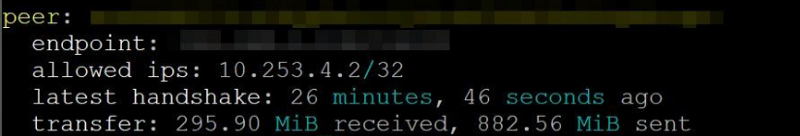
We modified our instance not to output this data. Under the hood, it’s known to WireGuard, but an operator (Windscribe) cannot see it very easily.
Miscellaneous
Other modifications include the ability to start Boringtun on a specific IP address, automatically bring up the WG interface, tweak the MTU, etc.
Protocol Support
At the time of writing, WireGuard is only available via manual configuration. Download a WireGuard config, and use it in the official WireGuard apps. This protocol will be natively supported in all our applications around the following dates:
- Android — End of July 2020
- iOS — End of July 2020
- Windows — Early August 2020
- MacOS — Early August 2020
- Linux — By the end of 2020
WireGuard supports all current Windscribe features like ROBERT, ability to connect on multiple common ports, and Static IP server support. What it currently does NOT support is port forwarding, but we have plans to introduce that in the near future.







