Ah, the world wide web, an absolute wonderland filled with puppies, kittens, memes, gifs, and trackers. While the rest of that list might be cute, cuddly, and relatively harmless, trackers are the reason Facebook knows what you have for breakfast every Tuesday, and why Amazon automatically sends you wet wipes every month because it knows you like your weekends messy.
Most of the time, you are “volunteered” into giving up all the little bits of info that contribute to a broad profile of who you are and what you’re into. Every “Accept Cookies” dialogue you’ve ever agreed to (with a list of conditions the size of Texas) is setting you up for exactly this type of snooping. However, profiling can also happen entirely without your knowledge, and oftentimes goes well beyond the boundaries of what is appropriate or ethical.
By the end of this article you’ll have a better understanding of what trackers are, why you should be wary of them, and how you can use Windscribe to eliminate them.
Cookies
When it comes to user tracking, profiling, and targeting, nothing is as ubiquitous as ye olde internet cookie. Cookies have been around since the first season of Friends (that’s 1994, for all my elder millennials out there). I mean, could they be any more of a classic? Anyway, that very year, Lou Montoli of Netscape Inc. thought up a new way of using an old UNIX programming trick (known as a magic cookie) on an internet still in its infancy.
Back in the 1950s, when computers occupied entire floors, a magic cookie was just a packet of information exchanged between two machines without changes being made to the packet upon changing hands.

Coming back to the present day, web-based cookies, like their edible counterparts, come in a variety of flavours. Allow me to walk you through the three most relevant types:
Session Cookies are meant to exist only in memory and, as the name suggests, expire after you end your browser session (you close the browser tab/window). These cookies store very basic information such as your preferred language and region, and aren’t generally malicious.
Persistent Cookies tend to stay on your computer for a set amount of time. Whether that’s for a few hours, days, or months, is entirely up to the site you’re visiting. An obvious example is the “remember me” checkbox present in every login screen ever. These cookies are also used to remember settings like language, theme, and other user preferences specific to the website being visited. Also known as “tracking cookies”, the information stored by Persistent Cookies can be used to spy on your browsing habits. The cookie Google sends your way every time you click a result on God’s own search engine™, is perhaps the web’s most widespread example of this.
Third-Party Cookies, by definition, belong to domains that are outside the one you’re actually visiting. These cookies are almost exclusively used by advertisers to track your usage patterns from one website to the next. Once you acquire a third-party cookie, it will follow you around the web and keep tabs on other ads presented by the same advertiser, so that it can report back home and tailor more ads you’re likely to click on.
Embedded Scripts
Embedded Scripts are used by advertisers to build a detailed profile of you. This is done by gathering freely available data being broadcast by your system (browser type, operating system, fonts, installed apps, etc). This furthers their understanding of how your mind functions,enabling them to predict what you might be inclined to buy.

Whereas cookies are a relatively passive means of tracking and profiling you, embedded scripts are of the hunter-killer variety. These scripts (tiny snippets of code) are more often than not, hidden in invisible visual elements on a page, called Tracking Pixels.
There are two types of tracking pixels out there: Retargeting Pixels track your usage pattern and communicate it to the next site you visit, and Conversion Pixels determine how and why you made the purchase you did, after the fact.
Assorted T(h)reats
The aforementioned methods have been on the radar of privacy advocates for a long time, and methods to combat them have come a long way. As with any arms race, advertisers have come up with novel methods of keeping tabs on netizens, and here we'll examine two widely used examples.
LocalStorage is a feature that was introduced via HTML5 way back in 2008. When used together with its cousin SessionStorage, a website can store up to 10 megabytes of tracking data on your machine until you either clear it out, or the website itself overwrites it. Compare that to the size of an average browser cookie, which is measured in kilobytes, and you begin to understand why this is a big deal.

Canvas Fingerprinting is another method based on HTML5. It uses the CanvasElement feature to draw a hidden image on a webpage. A hash (alphanumeric representation of the image) is then generated, and used to track the user without storing anything on the machine. The method used is the same for every computer, but due to hardware and software differences in each machine, a unique image is produced every time.
Stopping The Sugar Rush
Now that we’ve had a look at the sweet treats and creepy crawlies of the web, let’s move on to how you can keep your privacy and sanity intact. Despite the universally agreed upon open standards that the web is built on, your choice of web browser greatly impacts the level of initial privacy you’re afforded. We’ll begin by looking at two of the major players, then highlight further enhancements to be had via our very own Windscribe extension.
Mozilla Firefox
Firefox, produced by the open source software stalwart Mozilla Foundation, has been around for the better part of 20 years. The founding tenets of the organization (The Mozilla Manifesto) have always espoused privacy as a basic human right, and this is reflected in Firefox’s evolution as well as the foundation’s contributions towards the development of an open and fair internet for all.
Firefox’s Enhanced Tracking Protection feature provides users with protection against most of the aforementioned culprits right out of the box. Third-party cookies and LocalStorage are blocked by default for known tracking oriented domains. Users can also choose to lock down their browser environment even further by using the aptly named Strict Mode.

While it did not pioneer the ubiquitous Private Browsing mode found in every modern browser (that credit goes to Apple’s Safari), Firefox’s implementation of this feature has evolved over the years into one of the best in the business. Last but certainly not least, Firefox also includes protection from Fingerprinting via a blocklist that contains known sources.
As the brainchild of a non-profit entity, Firefox is inherently more trustworthy than most of the other players on the market. Alongside its huge library of extensions and support for all major mobile platforms, Firefox checks all the boxes for a privacy-first browser.
Google Chrome
Since its release in 2008, Chrome has surpassed all other browsers by charging its way to a whopping 68% of the global market share (as of 2021). The vast majority of Chrome's code comes from the open source Chromium Projects, which also includes the Webkit rendering engine. Webkit ironically enough, powers most of Chrome's competition except Firefox (which uses Gecko).
Chrome also pioneered browser security features such as Sandboxing (an industry first), and Safe Browsing, which is based off of Google’s list of domains that are linked to phishing, malware, fraud, etc. Most competing browsers also use this list for the same purpose. By leaning on its parent company’s gargantuan resources, Chrome has also spearheaded the web’s migration from HTTP to HTTPS.

All things considered, security is definitely one of Chrome’s strong suites. But how does Google’s Goliath stack up against Mozilla’s David when it comes to privacy? First and foremost, let’s consider that Chrome is brought to you by the biggest advertiser on the planet. To say that this puts it in murky waters regarding user privacy would be a massive understatement.
Chrome doesn't offer default protection against any of the cookie types we’ve discussed so far, nor does it restrict LocalStorage or prevent fingerprinting. By having the user associate their Google Account with Chrome browser, a large amount of usage data (location, search history and site visits) is also beamed back to Google HQ, and used to profile users within Google’s ecosystem an its external Ad partners.
Much to the chagrin of privacy advocates, Google also places the toggles to turn this off in obscure parts of users’ Account settings. Add to this multiple past violations of their own privacy policies, and you’ve got yourself a dicey proposition in a user-friendly package.
Windscribe
It would be a cruel world indeed if your choice of browser was the only thing standing between you and privacy hell. Luckily, both Firefox and Chrome support the use of browser extensions, which leaves room for others to step in and improve user experience.
Insofar as extensions go, Windscribe covers a lot of ground. Besides being an excellent proxy (allowing you to switch up your IP to a location of your choosing), our extension also incorporates the following privacy features to stand between you and the prying eyes on the interwebs:
Ad Crusher: Uses our curated in-house blocklists to block the vast majority of domains that broadcast ads on the web. The ability to whitelist specific domains is present should you want to support your favourite content creators with ad revenue.
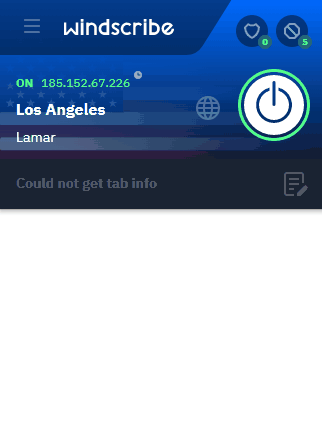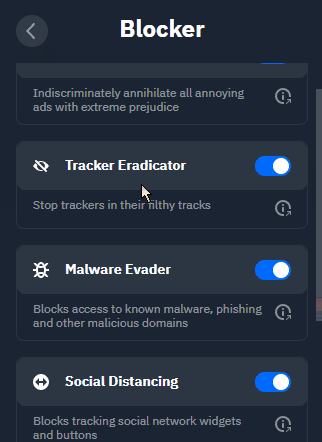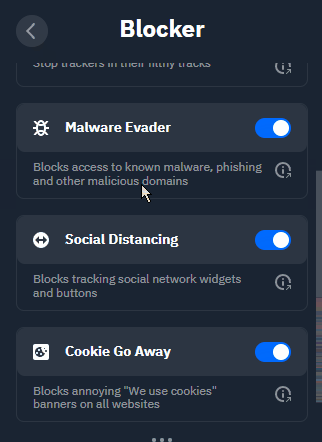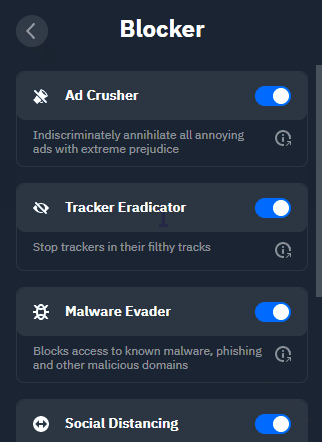
Tracker Eradicator: Gets rid of trackers without affecting your browsing experience using the same blocklists mentioned above. No relation to Dog The Bounty Hunter.
Malware Evader: Blocks access to known malware, phishing, and other malicious domains, in addition to the protection your chosen browser already provides.
Social Distancing: Blocks widgets from all the usual suspects (*cough* Meta *cough), and whatever other network happens to be in vogue with the kids that week.
Cookie Go Away: Blocks all the annoying “We use cookies” banners you see every time you visit a new website. At this point, I’m sure you’re well aware that everyone uses these damn things.
Cookie Monster: Remember Terminator 2? Well this is our T-1000. It keeps track of the cookies set by each browser tab, and depending on how you have it configured, deletes all 3rd party or 1st party cookies when you close the tab. Austrian accent not included.
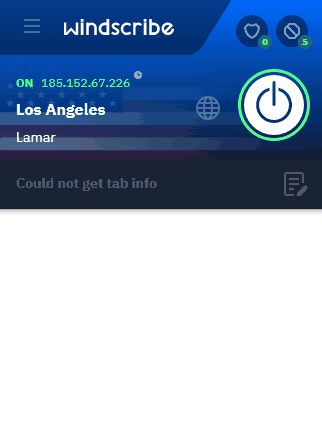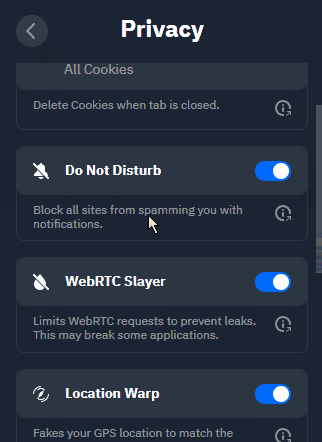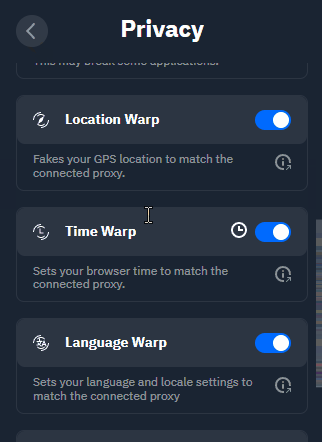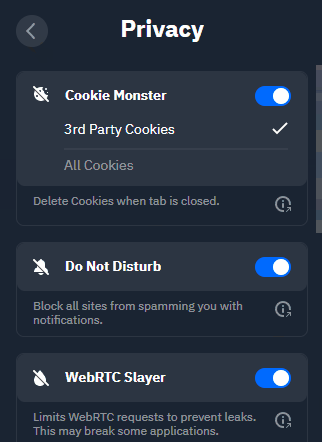
Do Not Disturb: Many sites request that you allow them to send you notifications. This permits them to spam you with OS level notifications, even when you're not browsing them. While this can have legitimate use cases, many sites abuse this browser API for marketing purposes.
WebRTC Slayer: WebRTC can be used to determine your actual IP address, since in browsers, those requests bypass proxy and VPN tunnels. This can deanonymize you. The WebRTC Slayer disables WebRTC altogether, so your browser does not snitch on you.
Location Warp: The location API in modern browsers bypasses a proxy or VPN, and returns your physical location based on GPS or Wi-Fi SSID name. Some services use it to "prove" that you're physically located in the location of your IP address. Location Warp tricks those services by providing fake GPS coordinates that correspond to the server location you're connected to.
Time Warp: Sites can detect the fact that you're using a proxy or VPN by checking the timezone that is configured in your browser. Time Warp will fake the time zone on your computer to match the time at server location you’re connected to, preventing this kind of detection.
Language Warp: Your browser language settings can also be used to determine your true location. If you're in Tokyo and connect to a proxy in San Francisco, the fact that your system language is Japanese is still available to the websites you visit. Alongside the other factors we’ve discussed, this can be used to determine your true location. Language Warp solves this by, you guessed it, spoofing your system language to match your proxy location.
Split Personality: Relax, this has nothing to do with your shitty ex. Each browser has what's known as a "User Agent" which identifies the operating system and the browser version you're using. When the Split Personality feature is enabled in the Windscribe extention, it will rotate your user agent between the most common ones out there, reducing the chance of basic fingerprinting.
Worker Block: Web/Service Workers don't allow the injection of content scripts, so they can still determine your browser's timezone and language settings. This feature will disable web/service workers inside your browser. This can break some websites, so don't enable this feature unless you know what you're doing.
The Last Bite
Given that the real world has most of us on edge these days, the nuances of online privacy and how it affects us might seem like something to be left simmering on the back burner. But as the real and virtual worlds become ever more entangled, being mindful of what you’re broadcasting to prying eyes, and doing something about it, is essential.
Download the Windscribe Extension here.

