
Many VPN services claim to “keep no logs”, but what does that actually mean? In many cases it means absolutely nothing since it’s a complete lie. Here are some recent examples of “no logs VPNs” that actually kept logs, despite their privacy claims:
- PureVPN Logs Helped FBI Net Alleged Cyberstalker
- IPVanish “No-Logging” VPN Led Homeland Security to Comcast User
These VPN providers were all named in publicly available court documents, so you don’t have to be HG Wells to imagine that instances like these are just the tip of the iceberg. In fact, it’s highly likely that many other VPN companies are keeping logs that they claim not to have, it’s just never been proven publicly.
Computer Science 101

Let’s take a closer look at the concept of logging. Firstly, it’s virtually impossible to operate any computer system (including the device you are reading this article on) without keeping logs. By logs I mean some kind of record that describes the state of a computer system. This includes virtually everything, but here are some examples:
- What applications are currently running
- Position of the browser window
- Amount of traffic sent through an interface
- That PornHub tab you have open right now
- The page your browser goes to when you click back
Keep in mind that these are just a few examples, there are hundreds more that I haven’t mentioned . These “logs” are usually stored in your computer’s memory, which is super fast, but suffers from a flaw — it loses data when power is disconnected. This is why most computer systems come with permanent storage (hard drive), where things can be saved for more permanent safe keeping. Windscribe’s servers work the same way, since they’re just computers that are architecturally identical to your PC, Mac, Android phone or TV.
What we store

States and logs can be split into 2 categories:
- Mandatory — things you absolutely must keep track of in order for the application or service to operate
- Nice to have — things that make lives of the operators easier, help assure the quality of the network and protect it against bad actors (and I don’t mean Tommy Wiseau).
Let’s talk about these in more detail in the context of Windscribe and our servers, and what it truly means to be a "no logs VPN".
Mandatory “logs”
When you connect to a Windscribe location, a VPN server is chosen by our app from the available pool of machines at that data center (you see data-centers, not individual servers). Windscribe then initiates a connection to the server and supplies a set of credentials that are linked to your Windscribe account. The same credentials you see when you use our config generator.
These credentials are verified to check for two things:
- If they are valid
- If they grant you access to the specific server
Windscribe currently uses the RADIUS protocol to handle this step. It’s likely that 99–100% of all other VPN providers use the same protocol for this step, as it’s identical for all VPN services.
The most common implementation of the RADIUS protocol is a piece of software called FreeRADIUS. It comes with a lot of bells and whistles, including bandwidth accounting, permanent session logging (including the source IP address of the client), and more. By design, it’s neither private or anonymous, as it’s meant for a vastly different use case than a privacy oriented service.
It’s for this reason that we don’t use any of those fancy features and have them all disabled. The only thing we currently use FreeRADIUS for is authentication and ACL enforcement. We had to build our own “privacy oriented” bandwidth and parallel connection monitoring system, which I’ll discuss in the next section. We also have plans in motion to replace FreeRADIUS entirely with a bespoke authentication system, which will allow us to store even less information, in a similar fashion to our write-less session token system.
After your credentials are verified and access to the server is granted (the app will say that you’re connected), the server has to keep track of the session in memory. This session record includes your source IP address, which resides in the the server’s routing table, as the server needs to know who the packets are coming from when you request something (like a web page), and where to send the packets to (when you download the webpage). Operating a VPN service without this is not possible.
This is not a huge privacy concern, as this data is never written to any permanent storage (hard disk), and resides in server’s memory which is flushed when you disconnect or when the machine is rebooted.
Had we been using the FreeRADIUS built-in accounting system, all this data would get transmitted to a central location and stored in a permanent database. Providers that claim to keep no logs may prune this database and remove records that are stale (user disconnected), but they don’t have to. This data can simply be archived forever, which is precisely what is meant by “connection logs”.
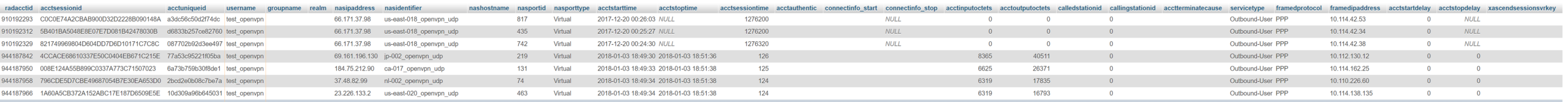
We used the accounting system built into FreeRADIUS ourselves (until February of 2018), except we modified our instance not to store the source IP addresses of the sessions, which may also be done by other “no-logging” VPN services, but we can never know for sure. PureVPN and IPVanish definitely didn’t do this, and that’s how they were able to cooperate with law enforcement.
The records in this connection table persist forever, so they must be cleaned up. We had a script that pruned this table every minute and removed records from stale connections. Is it possible to prove the existence of this script, or that it ran? No, it is not.
Nice to have logs
Outside of the mandatory basic information mentioned above, Windscribe stores the following pieces of data:
- Bandwidth used since your reset date
- What servers you’re connected to right now
- Timestamp of your last activity (accurate to a 12 hour window)
I’ll discuss each one in more detail.
Bandwidth usage
Each and every Windscribe VPN server runs an instance of OpenVPN (technically 2 instances) and StrongSwan. This facilitates connections via OpenVPN and IKEv2 respectively. Both applications have a command line interface which allow an external application to query the status of the server process. The status of the process also returns a list of active sessions that are currently connected and the byte counts of what was transferred during the session. This data resides in server’s memory (as mentioned previously), so it’s not very useful if it remains there, at the same time we don’t much care for most of this information, all we care about is how much data you used.
This data is fetched every minute, and the byte counts for each connected users are sent over to our central locations, where the API resides. It’s then stored in a Redis database, which exists entirely in server memory. This allows for super high speed lookups which are the basis of our abuse mitigation system as will be discussed later.
Parallel connections
Every time you connect to a Windscribe server, we have to verify your credentials to make sure you’re allowed access. Once that’s done, we need to be able to apply your R.O.B.E.R.T. settings, as everyone’s are different. In order to do this, we contact our API at the moment of connection, fetch this data, and configure R.O.B.E.R.T. in real time. The request to the API includes 3 pieces of information:
- Your username
- Server hostname
- RFC1918 IP address that was allocated for your connection, not to be confused with your actual WAN IP address, which we don’t care about
We store the last 2 parts in a Redis database, in a hash key that’s unique to every user. Once you disconnect from a server, a subsequent API call is made at that exact moment which notifies our API that you disconnected, and this record is immediately discarded from Redis. R.O.B.E.R.T. is also notified that you disconnected, which clears your custom configuration from its memory.
While you’re connected, we can count how many active connections you have, as well as which servers you’re connected to, by looking at your hash key. This data allows us to do some neat things which we’ll get into in a little bit.
Last activity
All our apps use the Windscribe API in order to login, fetch the server list, VPN configs and credentials. If your account is actively making API calls, that means you’re probably still using Windscribe, or at least have it installed and running. We store the timestamp of your last API call within a 12 hour window, as doing it for every request would introduce a heavy write load on our database — something we’d prefer avoiding.
How it’s used

So great, you have all this data, but why do you need to store this stuff in the first place? There are a few reasons:
Abuse prevention
We offer unlimited bandwidth and unlimited connections, however just like when you buy a soda at a movie theater that comes with “unlimited refills”, it’s going to be quite awkward when you show up with your entire family and everyone you know and demand 476,000 liters of Sprite. You will be politely asked to go away.
Windscribe is pretty similar, except we won’t be polite. A single Windscribe account is meant to be used by a single person, and I don’t mean your marital status either. It’s quite uncommon for individuals to be connected on 50+ computers, and 100+ phones at the exact same time. The bandwidth usage along with connection counts are used by our real-time monitoring system which looks at the “worst offenders” and makes a decision if this user is potentially abusive or not. Then a human makes a decision to ban the account or whitelist the “abuse” in case of a false positive.
If you share the account with your wife or brother, it’s likely fine, but that may set of a “sharing chain reaction” where they share it with someone, who in turn does the same. This is a sure way to get banned.
R.O.B.E.R.T. Syncing
When you make changes to R.O.B.E.R.T. on our website, and click on that sweet “ Apply to all connected devices immediately?” button, we need to know which servers you’re connected to, so we can notify R.O.B.E.R.T. running on those machines that your settings updated, and for R.O.B.E.R.T. to start enforcing the new set of rules. You can click here to learn about how R.O.B.E.R.T. works in detail.
Spam
Before you get your pitchforks, relax. The only thing Windscribe will ever spam you with is new Windscribe products, features, deals and those spicy memes. And we’re obviously using the term spam ironically, because everything we do is ironic, we also like saying ironic. What we mean to say is that we will gently and lovingly remind you of all the awesome stuff we are adding to our service via email and telepathy.
Windscribe doesn’t use any 3rd party services to ‘optimize our sales funnel.’ We believe that the limited data you entrust us with should stay in house, not transmitted to some 3rd party data mining company that will use it to train their (bullshit) AIs to deliver you more spam. In fact, we even use our own mail servers to send emails to avoid any of your information being sent to other businesses. This is in stark contrast to other VPN services that use 3rd party mailing services like SendGrid, Mailchimp, and Mailgun. Sure, these apps make it super convenient to manage email campaigns since you don’t have to worry about maintaining your own servers, IP reputation, monitor deliverability, etc. However, this convenience comes at the cost of customer privacy.
So what does this have to do with the data we store? Well, it allows us to send out customized emails in certain scenarios, for example:
- You signed up but didn’t use any bandwidth — Are you having problems? Did porn get unblocked in your country (yay for you!)?
- You didn’t use Windscribe in the last 6 months — Come back, we miss you!
- You are connected to 200 servers in parallel and used 300TB of data — Hey, you’re banned!
Well, there you have it. Now you know what Windscribe is up to behind the scenes! We know that there isn’t really any way for you to verify our privacy claims, and asking you to ‘trust us’ is asking a lot. Rest assured we have been hard at work developing a plan to allow tech savvy users to empirically verify our claims. Stay tuned.







