Navigating Journalism in China: A Comprehensive Guide To Reporting in the CCP's China
In China, journalism can be a matter of life and death. For many reporters, the stakes are incredibly high, caught between the need to tell the truth and the ever-present danger of state retribution.
So, I shall attempt to expose the harsh realities of journalism in China and highlight how we at Windscribe VPN can provide a crucial lifeline, as part of a robust privacy and security protocol. Having lived in China before and during COVID, I will draw from my own experiences as well as other real-life examples.
I will preface this by stating a VPN is only part of a proper threat model and those wishing to maintain their secrecy should consider the entirety of their network. If you would like some advice on how to achieve this please look to the end of the article where various tips have been included for your consideration.
If you're currently in China, and hopping over from the Great Firewall of China, you should give them a read for general best practice while accessing the internet in general.

The Tightrope: Reporting and Self-Preservation
Being a journalist in China is like walking a tightrope over a gaping abyss…with razor sharp teeth… picture the sandworm from Dune or Star Wars.
Due to the closure of numerous independent media outlets, the journalistic landscape has dramatically tilted in favor of state-run propaganda. This environment leaves little room for genuine reporting and poses substantial risks to those who strive for accuracy and objectivity.
For journalists and independent writers who dare to pursue unvarnished truth, essential tools like a secure VPN become crucial. By encrypting internet connections and masking IP addresses, VPNs can offer robust support against tracking and surveillance, preserving anonymity and personal safety in a climate where even the smallest misstep could be catastrophic. Assuming of course they're above board and not some national honeypot.
Real-Life Example: Chen Qiushi & Fang Bin
Former lawyer and citizen journalist Chen Qiushi gained recognition for his raw, eye-witness accounts of the early days of the COVID-19 outbreak in Wuhan. His disappearance in February 2020, as reported by The Guardian, underscores the dangerous terrain for journalists in China. While a friend of Chen Qiushi released a statement on his behalf to allay concerns, it is clear that there are real dangers for reporting in China. Fang Bin also provided many on-the-ground reports that also led to his detainment. In 2023 Fang Bin was released after 3 years in prison.

The Press Licensing System: Controlling the Narrative
China's strict media landscape is heavily regulated by a press licensing system that mandates journalists hold a "新闻记者证 - Xinwen Jizhezheng" (press card).
Introduced in 2009, these regulations aim to silence independent voices by providing legal foundations for gagging journalists. Writers who work outside these formal parameters face severe consequences, often experiencing not-so-fun interrogations in "Tiger Chairs." My own experience wasn't that bad. The chair was a bit wonky, they let me have a smoke, and honestly the officers didn't appear to personally have malice against me but they were stuck doing as they were told. Still, it's not something I'm looking to repeat any time soon and "Just following orders" can often lead down dark roads.
Despite having a VPN on my phone they didn't seem particularly bothered that I was circuvmenting the Great Firewall of China.
A 2020 report by the Committee to Protect Journalists offers insights into the state's methods designed to compel journalists to comply or face dire consequences. Using advanced VPN technology empowers these journalists by allowing them to remain incognito*, transmitting information securely without the immediate threat of detection.
*Providing an entirely robust threat model is followed.
Real-Life Example: Ai Weiwei
Prominent artist and activist Ai Weiwei faced relentless government scrutiny and arbitrary detention in 2011 for his outspoken criticism. His plight, covered by outlets like the BBC, serves as a stark reminder of what's at stake. For individuals like Ai, using digital anonymity tools can provide a vital layer of security.

China’s Global Image: Battling Bad Press
Internationally, China is often criticized for its human rights abuses, including its treatment of Uyghurs in Xinjiang and the mysterious disappearances of political opponents. In response, China has weaponized its media, adopting aggressive stances, particularly during the COVID-19 pandemic. According to a 2020 report by the Foreign Policy Research Institute, these efforts aim to reshape China's global image.
VPN services help journalists counterbalance these manipulative tactics by enabling access to multinational sources and uncensored data, thus providing a more rounded and accurate view of ongoing issues. By being able "hop the wall" or "翻墙", as its known, those in China can get a non-state mandated perspective on news, events, and viewpoints that can't be found domestically.
Real-Life Example: COVID-19 Whistleblowers
Dr. Li Wenliang, one of the earliest whistleblowers regarding the COVID-19 outbreak, faced significant censorship and persecution before his death, as reported by CNN. His challenges highlight the risks involved in speaking out. Such technology offers journalists a way to disseminate crucial information securely and accurately.
The Role of State Media During COVID-19
The pandemic showcased the extent of China’s media control, with state outlets casting their COVID-19 response as exemplary while criticizing other countries' efforts. The 2020 Reuters Institute for the Study of Journalism report documented this skewed media landscape. VPN services allow journalists to sidestep state propaganda by accessing undoctored and uncensored international sources of information, ensuring balanced news delivery.
Real-Life Impact: Citizen Journalism
According to the 2021 Citizen Lab report, numerous citizen journalists faced severe crackdowns for reporting on government inadequacies during the pandemic. Their sacrifices underscore the importance of these technological tools to protect and empower independent journalism. In 2024, Citizen Lab reported that many people are still unaccounted for.
Comparing State Media and Free Press
State Media vs. Free Press: What's the Difference?
Understanding the distinction between state media and a free press is critical for evaluating the integrity and independence of news sources. Each has unique characteristics and operational dynamics that substantially influence the type of content they produce. You may probably know someone who thinks that "All the press is the same" or "All media is biased" and whereas there's some truth to those statements it is incredibly disingenuous to leave your critical thinking there.
It’s also pretty damn lazy, too.
Here’s a comprehensive breakdown:
State Media
State media refers to media outlets that are directly controlled or heavily influenced by the government. The primary purpose of state media is to disseminate information that supports government policies and stifles dissent.
Characteristics
AKA: The Traits of Tyranny
- Government Control: State media operates under strict regulatory frameworks dictated by the government. Editorial decisions are often made in line with governmental policies and interests.
- Lack of Editorial Independence: Journalists working for state media rarely enjoy full editorial freedom. Reporting is constrained by the requirement to align with the government’s narrative.
- Promotion of Government Agenda: The content predominantly promotes the current government's achievements, often omitting or downplaying its failures and criticisms.
- Suppression of Dissent: State media can serve as a tool for quashing dissent and silencing opposing views, thereby limiting public debate.
- Propaganda Tool: These outlets are often used to instill specific ideologies and political beliefs in the public. The information disseminated is heavily biased, aiming to shape public opinion to favor the government.
- Censorship and Self-Censorship: Journalists may practice self-censorship to avoid repercussions, while the state imposes direct censorship to control the narrative.
Examples
- China: Outlets like Xinhua News Agency and China Central Television (CCTV) are overseen by the government, strictly following state-sanctioned narratives. Douyin/TikTok has become an excellent propaganda arm for this in China too. It's not just brain rot on there.
- Russia: RT (formerly Russia Today) operates under significant state influence, promoting content that aligns with Kremlin policies.
- North Korea: Korean Central News Agency (KCNA) serves as the mouthpiece for the state, broadcasting government propaganda. Though, unlike the above, I rarely see people falling for North Korean propaganda.
Free Press
A free press refers to media outlets that operate independently of government control. These organizations aim to provide unbiased*, diverse information, holding power to account and fostering public debate.
*Yes, I know. They still have biases, leanings driven from leadership, but let's be adults and act in good faith when discussing these topics.
Characteristics. AKA: Dealings afforded by Democracy
- Editorial Independence: Free press organizations exercise full editorial freedom. Journalists can investigate and report on issues without undue influence from external entities.
- Diverse Perspectives: These outlets present a variety of viewpoints, encouraging a balanced and multi-faceted public debate.
- Accountability and Transparency: Free press holds both public and private sectors accountable by exposing corruption, inefficiency, and misconduct.
- Investigative Journalism: A hallmark of the free press is its commitment to in-depth investigative journalism. Reporters are dedicated to uncovering truths that those in power may wish to conceal.
- Public Service: Free press serves the public interest by providing crucial information that aids citizens in making informed decisions.
- Self-Regulation and Ethical Standards: High ethical standards and self-regulation mechanisms ensure responsible reporting. Issues like libel and defamation are carefully navigated to maintain credibility and trust.
Examples
- United States: Outlets like The Associated Press, The New York Times, Washington Post, and CNN operate independently, reporting diverse viewpoints and holding power to account. I am expecting flak for these examples but I can't win either way here.
- United Kingdom: The BBC, despite being publicly funded, maintains editorial independence, often scrutinizing government actions and policies. As a Brit I want to make some personal comments here about recent failings but it'll serve as an example for now.
- France: Le Monde and Agence France-Presse (AFP) operate free from government control, offering a wide range of perspectives and critical reporting.
Key Differences:
"All media is the bloody same!" It can feel like that I'm sure but here are some important points of difference.
- Control and Influence:
- State Media: Directly controlled or influenced by the government, often following stringent guidelines.
- Free Press: Operates independently, with editorial decisions made without government interference.
- Editorial Freedom:
- State Media: Restricted, limited to promoting government-approved narratives.
- Free Press: Unrestricted, allowing for critical and investigative reporting.
- Purpose:
- State Media: Designed to support and promote government agendas, often at the expense of transparency and accountability.
- Free Press: Dedicated to serving public interest by providing truthful, unbiased information, holding power to account.
- Content and Bias:
- State Media: Content skewed to favor the government, often excluding or misrepresenting dissenting views.
- Free Press: Strives for balance and inclusion of multiple perspectives, though may still exhibit some biases based on ownership and funding sources.
- Accountability:
- State Media: Rarely holds the government accountable, working to maintain the status quo.
- Free Press: Actively works to expose corruption and wrongdoing in all sectors, fostering a culture of accountability and transparency.
Understanding the fundamental differences between state media and a free press is essential for evaluating the integrity, bias, and reliability of national and international news sources. In an increasingly interconnected yet blurred world, discernment in media consumption is vital for an informed and engaged society. Bit of a mouthful, but I want to hammer home the points above so we can continue with a shared perspective.
The Impact of Media Policies on Public Perception
In China, government-imposed media policies shape public perception by creating a tightly controlled narrative. According to the RAND Corporation’s 2018 study, this manipulation leads to a misinformed public less likely to question governmental actions. Secure internet technology helps journalists access uncensored global news sources, enabling the spread of balanced information and fostering an informed public.
Real-Life Example: Russian Election Coverage
During the 2018 Russian Presidential election, state media heavily favored Vladimir Putin, impacting public perception. Studies by the European Journalism Observatory reveal the consequences of state-controlled media on democratic processes. Reliable security and privacy tools provide the means to counter such biases.
The Future of Journalism in China
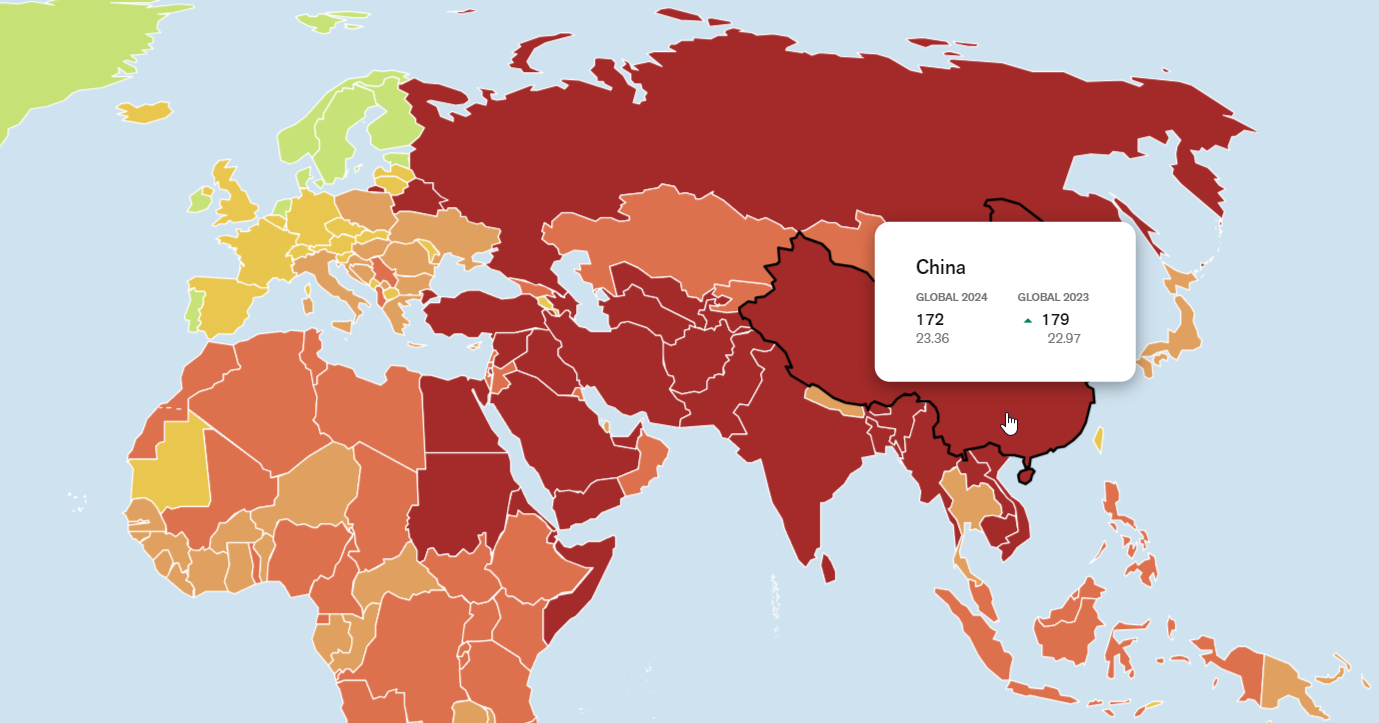
The future of journalism in China appears bleak as state control tightens further. However, press freedom advocates, both local and international, must persist in pushing for transparency and independence. The Reporters Without Borders 2021 Index ranks China near the bottom in terms of press freedom, highlighting the urgent need for reform. With fake news drowning out actual news and facts the need is greater than ever.
A lie can run around the world before the truth has got its boots on - Terry Pratchett
The above quote is from one of my favorite novels (The Truth), written in 2000. Sir Pratchett has been proven entirely correct as a study by MIT in 2018 showed that fake news is likely to circulate up to 6 times faster than the truth. GNU Terry Pratchett.
Advanced digital security remains a critical tool for this struggle to help the truth get its boots on, providing journalists with a secure channel to bypass censorship and share accurate accounts.

Digital Surveillance and its Impact on Journalism
China employs pervasive digital surveillance, from facial recognition to monitored social media, fostering a culture of self-censorship. A 2019 Citizen Lab report details how these measures make it arduous for journalists to operate freely. Secure browsing options offer robust encryption and anonymity, essential for maintaining confidential communications.
Real-Life Example: The Golden Shield Project
China's Golden Shield Project poses significant threats to digital rights and journalistic freedom, as highlighted by the Carnegie Endowment for International Peace. With advanced encryption, journalists can navigate this hostile environment more securely. The Great Firewall of China, as it is affectionately known, doesn't just stifle the internet. It actively hinders effective communication from China to the outside world. Often preventing citizens from highlighting examples of human rights abuses or other injustices.
International Reactions and Sanctions
International bodies continually respond to China’s media controls with sanctions and diplomatic pressure. The United Nations Human Rights Council's 2020 resolution critiques China’s stringent media controls, urging adherence to international standards. Secure communication services enable journalists to document these international reactions, bolstering global awareness and pressure for change.
Real-Life Reaction: U.S. Sanctions on Chinese Media
In 2020, the U.S. imposed sanctions on multiple Chinese state-run media outlets, detailed in a report by Reuters. These digital tools facilitate real-time reporting on such international measures, ensuring crucial information reaches a broader audience.
Case Studies
Real-life examples underscore the severe challenges journalists in China face daily.
Zhang Zhan
Zhang Zhan was sentenced to four years in prison for reporting on the COVID-19 outbreak in Wuhan. Coverage by The New York Times highlights the dangers involved in this profession. Digital security measures help shield journalists from detection, enabling them to continue their essential work securely.
Role of Social Media
Social media in China intermittently allows for the dissemination of independent viewpoints, though such accounts are swiftly censored. A 2020 Freedom House report discusses how platforms like WeChat, Douyin, and Weibo offer brief moments for free expression before heavy-handed censorship. Secure private browsing enables users to navigate these platforms safely, ensuring their voices are heard before being silenced.
Douyin, with its Western variant TikTok, has become the de facto delivery method of soft-power propaganda. Often highlighting glamorous travel shots, positive stories, and downplaying tragedies that happen within China. It is a suitable method of downplaying accusations leveled against China and a much better approach than the previous aggressiveness shown with wolf-warrior tactics.
Real-Life Social Media Example: Weibo Censorship
Weibo frequently censors sensitive conversations, such as political protests, documented by Amnesty International. Secure browsing is essential for sharing unapproved content and ensuring stories reach the public eye.
Challenges Reporters Face in China
Journalists in China confront a slew of significant challenges:
- Surveillance: Intense digital monitoring.
- Censorship: Stringent regulations and press card requirements.
- Harassment and Detention: Risks of imprisonment and harassment.
- Physical Threats: Government-enforced interrogation tactics.
- Suppression of Stories: Forced alteration or removal of critical news.
- Digital Restrictions: Internet censorship and restricted access to foreign media.
- Legal Perils: Coerced confessions, biased trials favoring the state.
- Loss of Resources: Limited access to crucial investigative tools and information.
Real-Life Example: Huang Qi
Huang Qi, a Chinese human rights activist and founder of the 64 Tianwang website, is one such journalist who faced intense persecution. According to a 2019 Human Rights Watch report, Huang was sentenced to 12 years in prison for his reporting activities, showcasing the severe consequences Chinese journalists can face. Secure browsing tools would have been pivotal in protecting his work from government scrutiny.
What does the future look like for journalists reporting in China?
Journalism in China is rife with daunting challenges and immense personal risk. By detailing these intricacies and providing real-life examples, this article highlights the irreplaceable role of advanced VPN services in aiding journalists.
By bypassing censorship, accessing global news, and securely sharing stories, such tools are essential for continuous, truthful journalism amid pervasive governmental control. Their utility is indispensable in the fight for a free, independent press in oppressive regimes like China.
These examples are of real events. Real people. This isn't some dystopian future...these dystopian events have already happened.
What would your average Threat Model for a Journalist in China look like?
Device Security
- Secure Your Bloody Devices:
- Encryption: Encrypt all devices, including laptops, smartphones, and external storage. Use strong encryption standards like AES-256.
- Secure Boot and BIOS Settings: Enable secure boot options and password-protect BIOS settings to prevent unauthorized access.
- Use Vetted & Trusted Hardware:
- Purchase Variants Without Predetermined Settings: Obtain devices from reliable vendors and avoid second-hand or potentially compromised hardware.
- Anti-Tamper Measures: Use tamper-evident tools to check if devices have been physically tampered with (e.g., tape seals).
- Operating System (OS) Hardening:
- Regular Updates: Ensure that the operating systems of all devices are up to date with the latest security patches.
- Minimalist Approach: Opt for operating systems known for security, such as Qubes OS or a well-configured Linux-based OS.
- Application Security:
- Use Security-Focused Software: Install only trusted applications and regularly update them. Tools like Signal for messaging and Tor for browsing can offer enhanced security.
- Application Whitelisting: Configure systems to allow only whitelisted applications to run, reducing the risk of unauthorized or malicious software.
- Password Management:
- Strong Passwords: Use complex, unique passwords for all accounts and change them regularly.
- Password Manager: Utilize a trusted password manager to store and manage your passwords.
- Two-Factor Authentication (2FA):
- Enable 2FA: Use two-factor authentication for all critical accounts and services for an added layer of security.
- Phone Profiles & Accounts
- Consider a new Google profile for your account as opposed to using an older one which is linked to your contacts.
- For iOS users needing to bypass restrictions:
- New Non-Regional ID: Register a new ID instead of switching regions.
- Avoid shared/public IDs when using these new credentials.
Network Security
- VPN Use:
- Windscribe: Consistently use a reliable VPN like, say I don't know, Windscribe to encrypt internet traffic and mask IP addresses, preventing potential interception.
- Multiple Exit Points: Use multiple exit points to reduce the risk of geolocation tracking.
- Secure Communications:
- Encrypted Messaging: Communicate using end-to-end encrypted messaging apps such as Signal.
- Encrypted Email: Use PGP or other forms of encryption for email communication. Services like ProtonMail offer integrated encryption.
- Anonymous Browsing: Use Tor Browser to obscure browsing activity from potential surveillance.
- Encrypted proxies (Shadowsocks/V2Ray/Trojan) have a steeper learning curve but their effectiveness cannot be discounted.
- Public Wi-Fi Precautions:
- Avoid Public Networks: Refrain from using public Wi-Fi networks. If unavoidable, ensure that VPN is always activated.
- Create Safe Hotspots: Use mobile data with your device’s hotspot to create more secure personal networks when mobile.
- eSIMs that utilize foreign (non-domestic) networks are a more sensible option than domestic Chinese ones.
Physical Security
- Operational Security (OpSec):
- Travel Plans: Keep travel plans confidential. Use encrypted communication if discussing travels.
- Disguise Digital Footprint: Regularly change locations and patterns to avoid creating detectable digital footprints.
- Secure Storage:
- Secure Backups: Store backups in secure, offline locations. Use robust encryption to protect backup data.
- Emergency Data Destruction: Ensure devices have secure erase functions for emergency situations where data needs to be quickly destroyed.
- Anti-Surveillance Measures:
- Awareness of Surroundings: Be vigilant of your environment to detect any physical surveillance.
- Discrete Technology Use: Use nondescript devices when working in public to avoid drawing attention.
Legal and Social Shielding
- Legal Considerations:
- Understand Local Laws: Keep abreast of local cyber laws and ensure compliance to avoid unnecessary legal entanglements.
- Have Legal Support: Cultivate a network of legal professionals who specialize in cyber law and human rights to provide emergency legal assistance.
- Identity Management:
- Use Pseudonyms: Reporting under pseudonyms or anonymously can reduce personal risk.
- Data Minimization: Only carry essential information and documentation. Safeguard personal identifiers (e.g., passports or identity cards) securely.
- Anonymous Publishing:
- Drip Feed Information: Gradually release sensitive information to prevent the complete scope of work from being compromised if caught.
- Secure Collaboration: Collaborate with international media organizations to guarantee the safety and timely publication of sensitive stories.
Developing and adhering to a robust threat model is essential for journalists operating under oppressive regimes. By leveraging tools like Windscribe and adhering to recommended security practices, journalists can significantly mitigate risks and sustain the crucial role of independent reporting.I know, I know. We're biased. Of course we're going to recommend ourselves as a VPN provider. But hear me out: We are the only VPN to feature a method to deal with Traffic Correlation Attacks - a solution we developed to help shield activists, reporters, and whistleblowers as requested BY said people.
What are Traffic Correlation Attacks?
These tactics are used to correlate seemingly anonymous online behaviors with specific individuals, often used by governments or malicious entities to de-anonymize users in high-security environments like China. Here’s how Windscribe helps mitigate the risk of traffic correlation attacks among other tools and some best practices for journalists:
How Journalists Can Improve Their Threat Model
1. Decoy Traffic / Combat Mode:
- As previously mentioned we have our Decoy Traffic Mode which is purposely designed as a defense against Traffic Correlation Attacks. This is done by fabricating bursts of activity to mask your actions. Be aware this uses a lot of data to achieve this.
2. Double Hop:
- Windscribe’s Double Hop feature routes your connection through two different VPN servers. This significantly complicates traffic correlation by adding an extra layer of separation between the user's entry and exit points. By masking your IP address multiple times, it becomes increasingly difficult for an attacker to correlate traffic.
3. Split Tunneling:
- Configuring Split Tunneling to route only sensitive traffic through the VPN while non-sensitive traffic uses the regular internet can help reduce patterns that might be used in correlation attacks.
4. Stealth Mode:
- Stealth Mode hides VPN traffic from deep packet inspection (DPI) technologies. By obfuscating VPN traffic to look like regular HTTPS traffic, it makes it harder for entities attempting to correlate VPN user traffic based on protocol analysis.
5. Randomized IP Transmission:
- Windscribe periodically switches your IP address, making it more challenging for observers to link varying traffic to a single source.
Best Practices
1. Use Multiple VPN Providers:
- For the highest level of security, journalists can route their traffic through several VPN providers in succession (known as ‘VPN chaining’). While Windscribe offers robust protections, adding extra VPN layers through different providers makes correlation attacks exponentially more complex.However, with the VPN market being filled with chancers and frauds I don't have many suggestions for whom you should use alongside us. You can use the VPN Map as a tool to help you make your own decision.
2. Tor Over VPN:
- Combining Tor with Windscribe can provide an extra layer of anonymity. Connecting first to Windscribe and then to the Tor network can obfuscate the origin IP address further, complicating any attempts at traffic correlation.
3. Consistently Use Encrypted Services:
- Always send and receive data over encrypted channels, be it via HTTPS websites, encrypted messaging apps like Signal, or encrypted email services. End-to-end encryption can prevent correlation even if traffic is observed both at the VPN entry and exit nodes.
4. Be Mindful of Digital Fingerprints:
- Regularly clearing cookies and using browser settings that minimize the digital footprint can reduce the risk of traffic correlation. Tools like browser plug-ins which block trackers help maintain anonymity.
5. Avoid Repetitive Behavior Patterns:
- Changing online routines and avoiding consistent time patterns can make your digital behavior less predictable and harder to track.
6. Network Segmentation:
- Use different networks for work and personal usage. For instance, using cellular data hotspots for sensitive work while relegating personal browsing to a home or public Wi-Fi while shielded by Windscribe helps obfuscate correlation.
What to Expect in China
Let's face it, using VPN services or proxies based in China should be a no-brainer at this point. But just in case…
No Privacy
- Privacy and Security Ignored: China-based VPNs practically treat your privacy like discarded takeaway wrappers.
- No Zero-Log Policy: Forget about "zero-log" guarantees; they're jotting down every cat video you watch.
Legal Shenanigans
- Compliance with Chinese Laws: Some providers actually require users to be good little citizens and obey Chinese laws.
- No Refund Policy: They’ve got a strict no refunds policy—like a dodgy car boot sale.
- Real-Name System Reliance: These services love China's real-name registration system almost as much as you love your pet rock.
Here Come the Cops!
- Risk of Crackdowns: Susceptible to sudden government crackdowns—one day they’re there, next day they’re gone.
- Content Restrictions: They enforce content restrictions like a librarian with an overzealous attitude.
- Access Restrictions: Limitations on what sites you can access, because why would you want unrestricted information?
- Data Leaks: Your data leaks more than a sieve.
- Police Submissions: Operators might hand your data to the police, just like that nosy neighbor.
- Intentional Exposure: They expose your personal info during disputes—real mature.
- Data Selling: Some operators are more interested in selling your data than safeguarding it.
Avoid Unreliable Freebies
- No Go on Chinese App Stores: Don’t download free VPNs from Chinese app stores, Android markets, or dodgy websites. Just nope.
- No Shared/Public Nodes: Avoid Shadowsocks shared or public nodes unless you're desperate.
- Say No to Shady Services: Dodgy VPNs with privacy issues? Hard pass.
Keep Your Device Clean
- Non-Chinese ROMs for Android: Stick to non-Chinese ROMs for Android devices like they’re your best mate.
- Avoid Chinese Software: Don’t clutter your devices with 360, QQ, WeChat, or other Chinese software unless you enjoy being watched.
Anonymity and Payment Fortification
- Avoid Domestic Payment Platforms: Skirt around Alipay, WeChat Pay, or UnionPay for buying VPN services—like a seasoned dodger.
- Use Cryptocurrencies and Foreign Methods: Opt for Bitcoin, USDT, foreign PayPal accounts, or bank cards issued outside of China—keep it global.
- Tor Browser: Fire up Tor Browser for web browsing to obscure your browsing history from the eyes of the proxy service provider.
- Strengthen Anonymity: Bulk up your anonymity when registering and using overseas services.
How Windscribe Helps with Shortcomings of Traffic Correlation Attacks
1. No Logs:
- Even if traffic is correlated, Windscribe’s no-logs policy ensures there isn’t any stored data that could connect your identity to your activities.
2. Trusted Server Deployment:
- Windscribe builds its servers with trusted configurations and regular audits ensuring that even if someone tries to compromise a server, they won’t succeed in retroactively analyzing traffic to identify users.
3. VPN Obfuscation Techniques:
- Minor latency adjustments and packet shaping infrastructures that Windscribe continually refines make it increasingly challenging for an attacker to successfully relate incoming and outgoing traffic to a single identity.
4. Diskless RAM-Only Servers
- Our Diskless RAM only stacks mean that nothing is stored locally. As a VPN with experience with server seizures, and authorities recovering nothing, we're not only proven but have used that experience to ensure the highest possible level of security.
While no system can be entirely fool-proof, adopting Windscribe's array of robust security features, in combination with mindful online behaviors, greatly minimizes the risks. For journalists working under intense scrutiny, leveraging these technologies and best practices ensures the highest possible chances of maintaining their anonymity and security.
Looking for a guide to reliably navigating China in Mandarin?
We highly recommend this resource for detailed methods and advisories
Know a journalist in need? A whistleblower that needs saving? An activist in trouble?

At Windscribe, we strongly believe in the freedom of the internet for all. We're anti-censorship, we're for Freedom of the Press, and we don't just say these things.
We build our entire identity around these principles.
WINDSCRIBE PROVIDES FREE PRO LICENSES TO JOURNALISTS, NGOS, AND REPORTERS.
Share the above with those in need and we'll be sure to provide them with what they need so they can continue to make the world a better place.





